THREATGET administration
THREATGET essentially consists of two components. On the one hand, we have the Enterprise Architect plugin. The system model can be modeled in this and the analysis can then be carried out. On the other hand, we have the Web Interface which provides the possibility to define diagram components and rules.
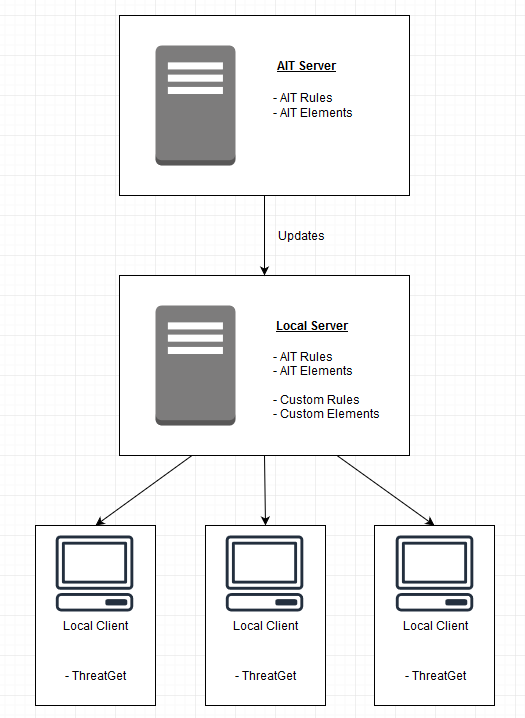
The system model is built from previously defined Elements, Boundaries and Connectors. These diagram components are created and managed within the web interface. Their properties, the so-called Tagged Values, can also be defined and referenced there. These diagram components are stored in the local server. The AIT provides updates for these components, which are loaded from the AIT server to the Local server. You can also define your own diagram components inside of the Web Interface of THREATGET. This enables you to adapt your system model to your needs.
If you have never created a diagram component, we recommend doing the TUTORIAL.
In addition to the system model, the rules are the most important part for an analysis. Just like the diagram components, the rules are created and maintained in the Web Interface. The AIT provides a comprehensive catalog of rules for download. This catalog is also constantly being expanded so that your analyzes are becoming more and more effective. You can also define your own rules inside the Rule Editor
To learn how to create a rule we recommend to follow the rule TUTORIAL.
The following diagram is intended to illustrate what the general structure of THREATGET looks like. The local server is centrally located and stores the defined rules and elements. The AIT Server provides the local server with updates. The individual local clients use the local server to call up the defined diagram components for the system models.