Introduction to ThreatGet
This section introduces ThreatGet and demonstrates how to develop a small example. However, before we can model an example, we should first create a project, followed by a ThreatGet diagram.
Creating a project
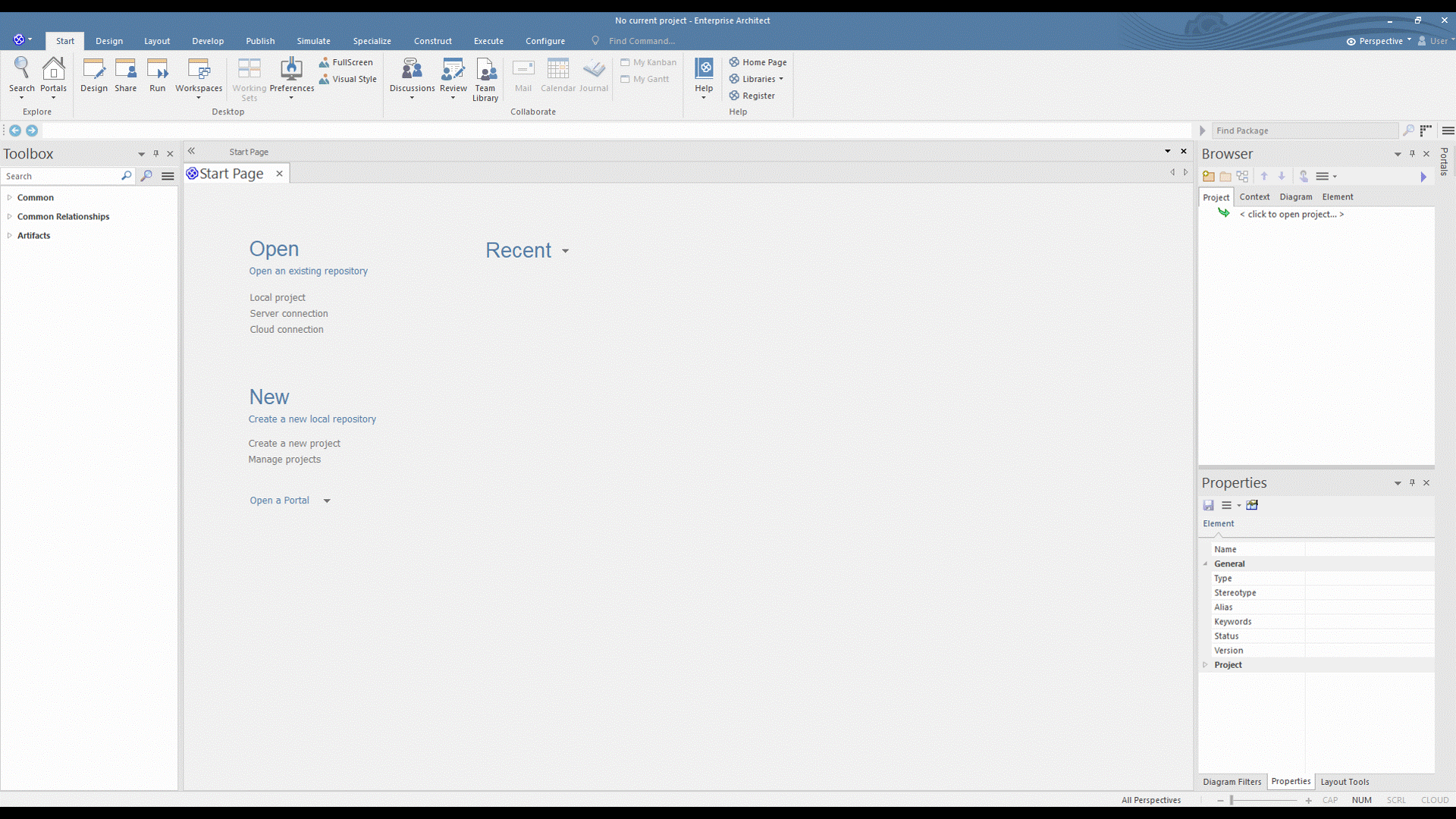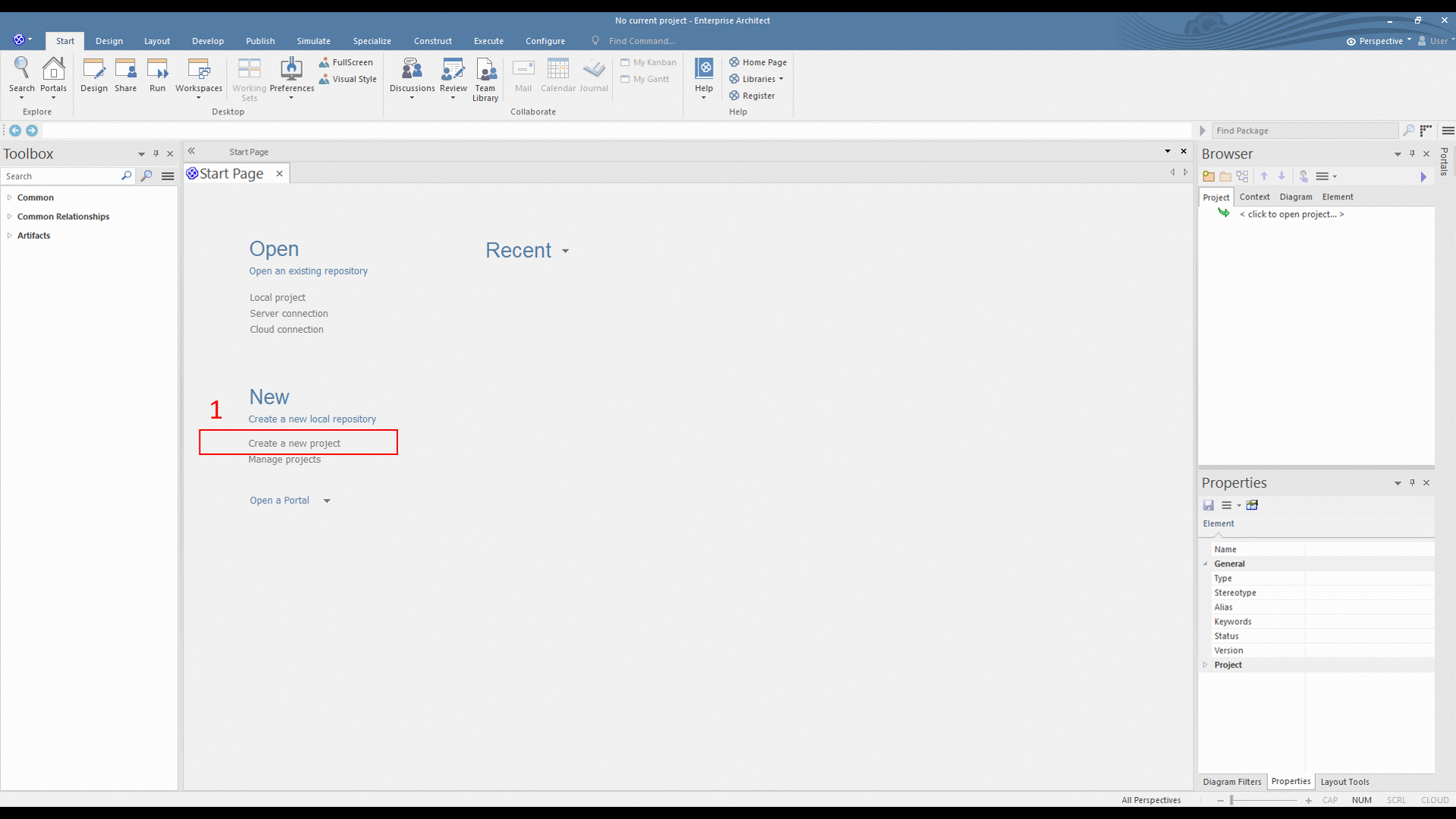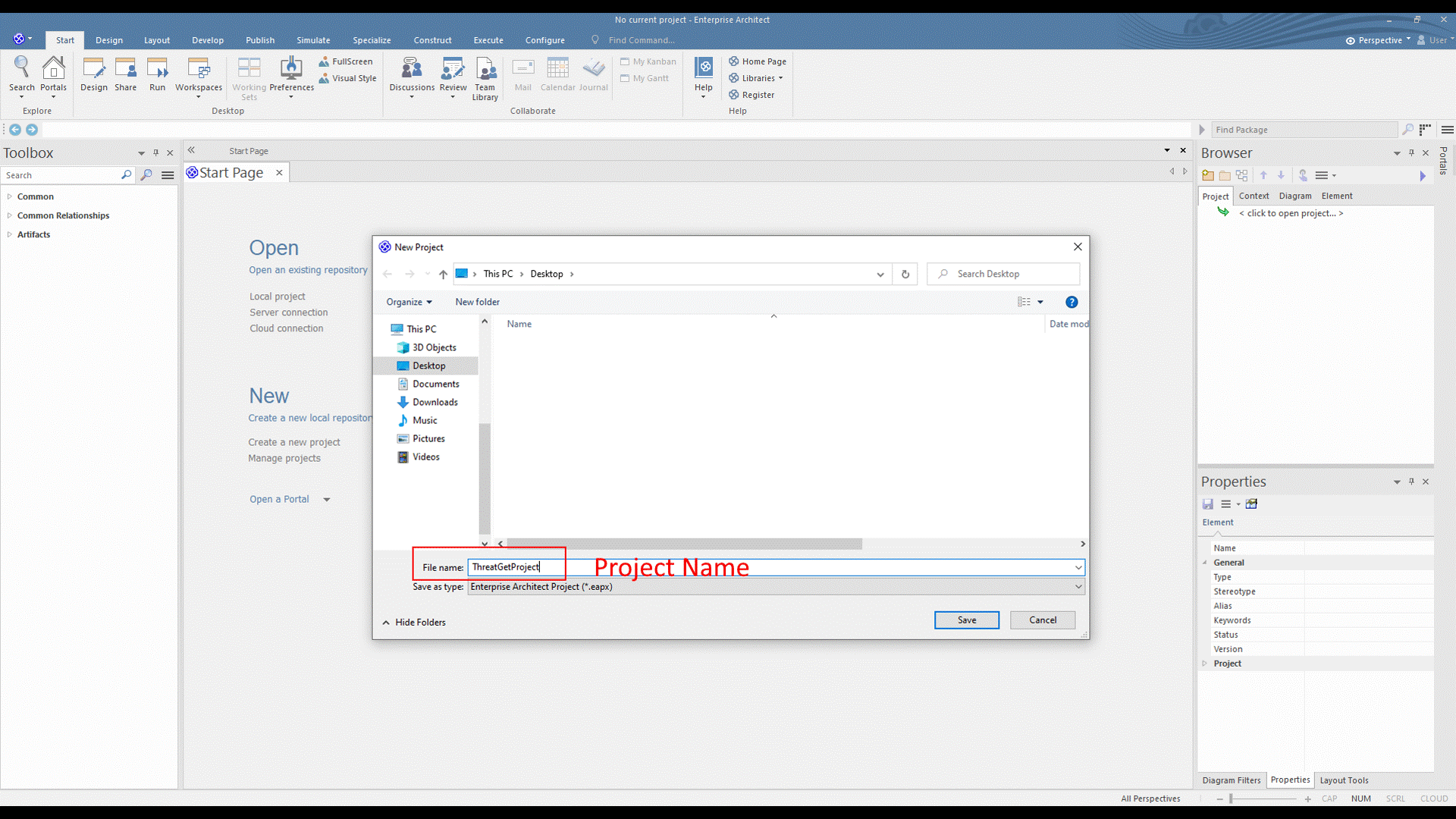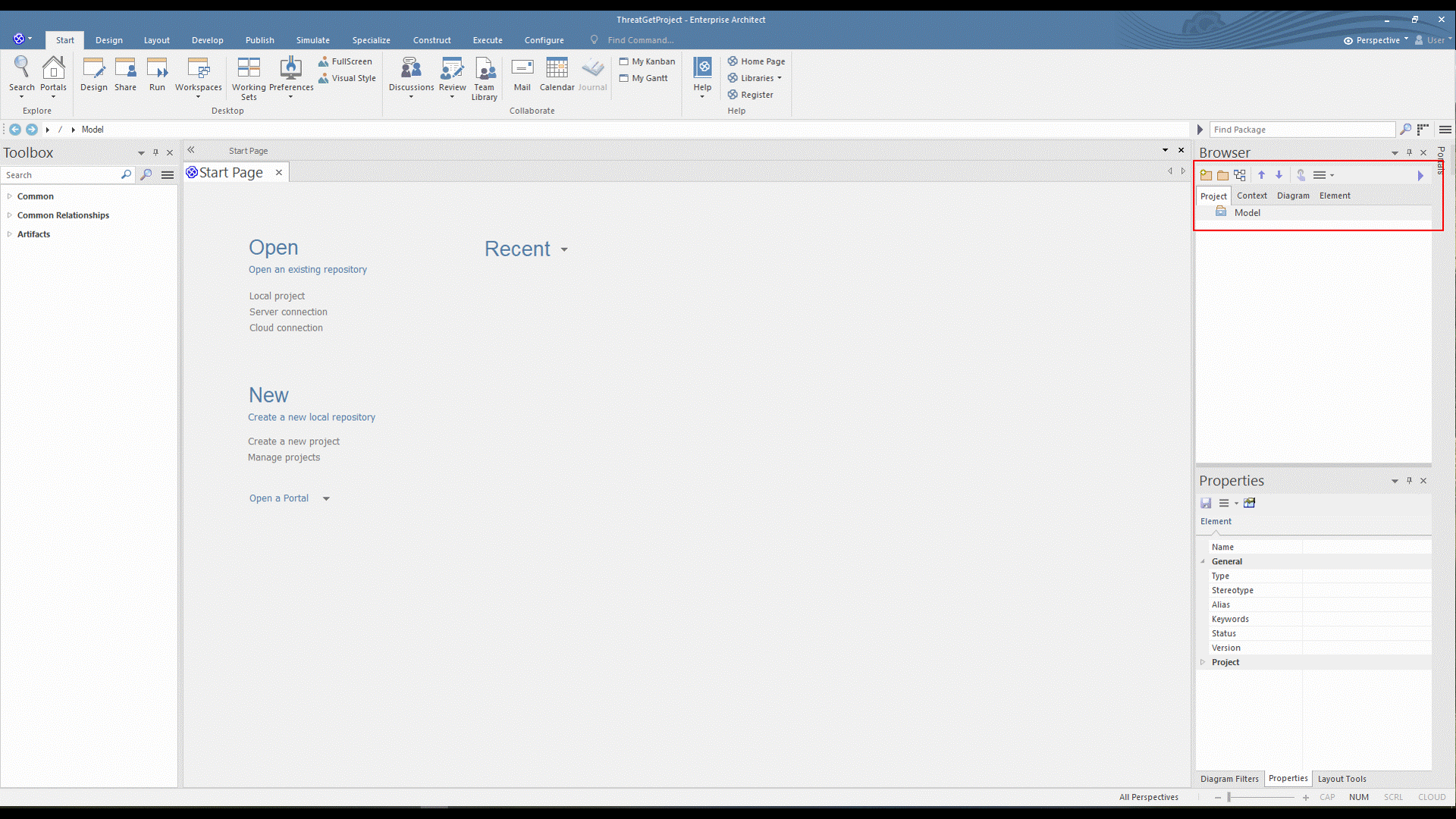
The first step is creating an empty project that aims to store, manipulate, and manage one or multiple models. A new project is created from the EA's "Start Page" or the top menu.
Creating a diagram
The next step is to add a model; this can be done by right-clicking the Model from the Project Browser and then clicking on Add a Model using Wizard, as shown below.
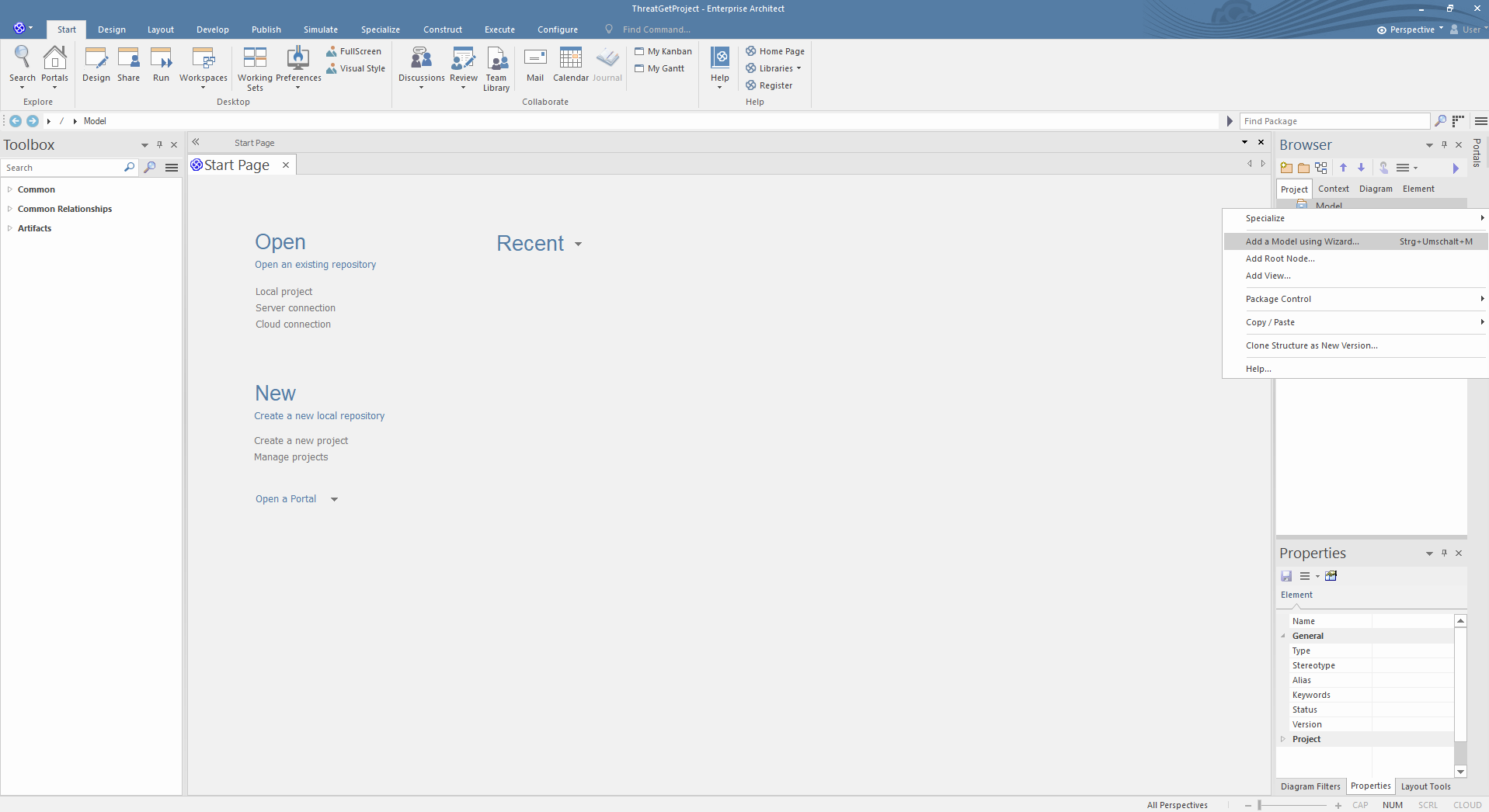
You can choose between two THREATGET diagrams. Please select THREATGET Diagram and click on Create Pattern to create an empty diagram. You can model in the THREATGET empty diagram with elements, connections, boundaries, and tagged values.
The THREATGET Diagram with Example is a pre-defined THREATGET AIT-model that contains elements, connections, and tagged values from the THREATGET Toolbox. It also includes a model description. This diagram is a reasonable basis for the first execution of THREATGET.
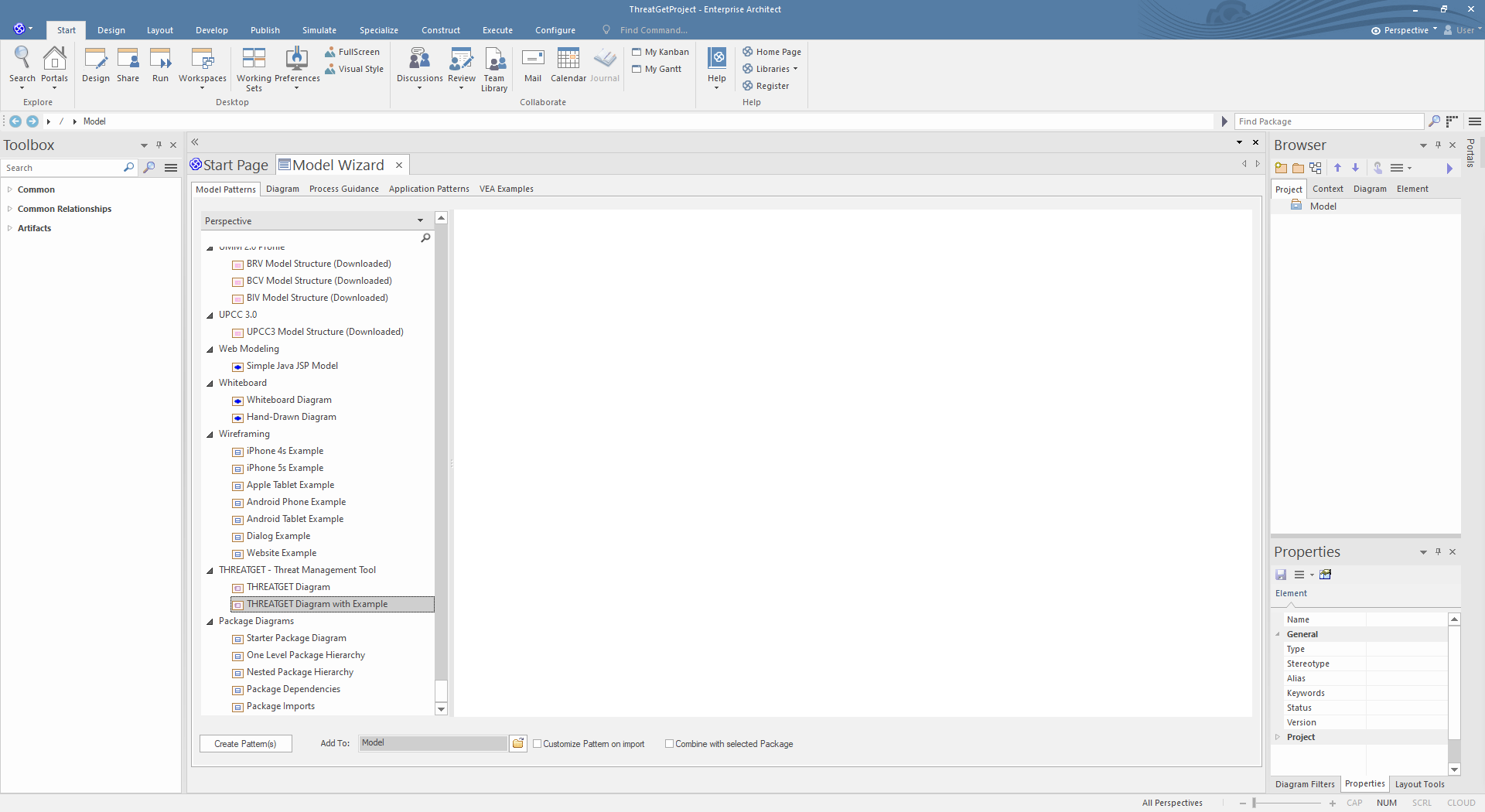
You can now open the default example by expanding the Model and then THREATGET Example and double-clicking on Threat Model.
Note: If you can not see the THREATGET model variations in "Add Model Using wizard ...", then check your ThretGet installation & server configuration
Creating a new ThreatGet model is described as follows.

Modeling a simple example
This section provides an overview of how to use ThreatGet to create a simple example. The following diagram depicts a high-level representation of the ThreatGet model that needs to be designed.
The model depicts that the Vehicle1 communicates with the Vehicle2 by sending data represented as a critical asset to the other vehicle (i.e., Vehicle2). The Vehicle2 receives data via the Wireless Interface and forwards it to the Main ECU for processing and controlling the vehicle move via the Brakes. A boundary is defined that encompasses all elements. The following video shows steps for creating this model on ThreatGet using its elements, connectors, assets, and boundaries.
We are now ready to perform a threat analysis.