Report Generation
Once the threat analysis process is completed, we can generate full documentation that includes all the analysis outcomes.
To generate a report, click on the Print Report button, as shown below.
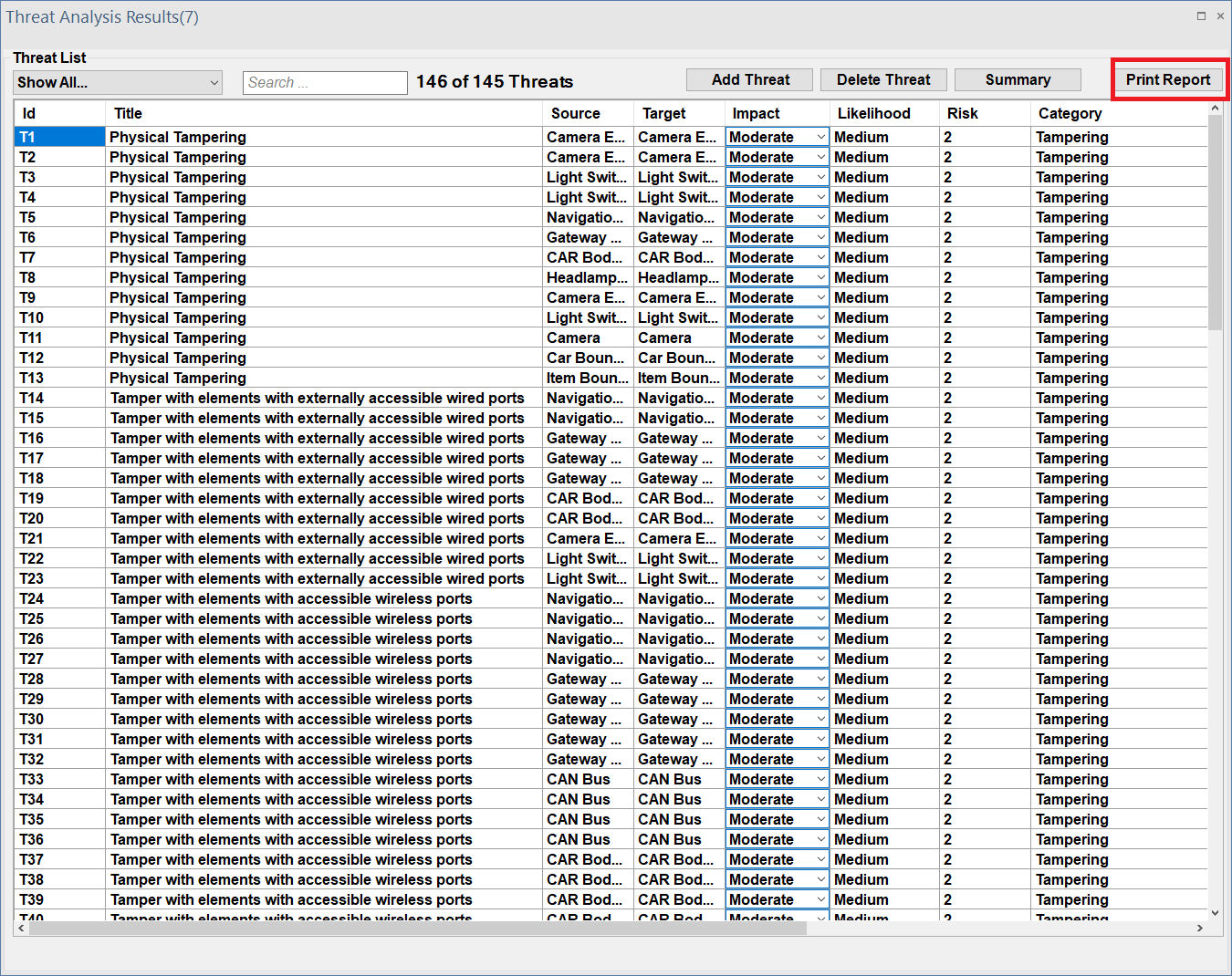
This opens the Report Generation dialog. Users can select which threats should be included in the final report through the dialogue.
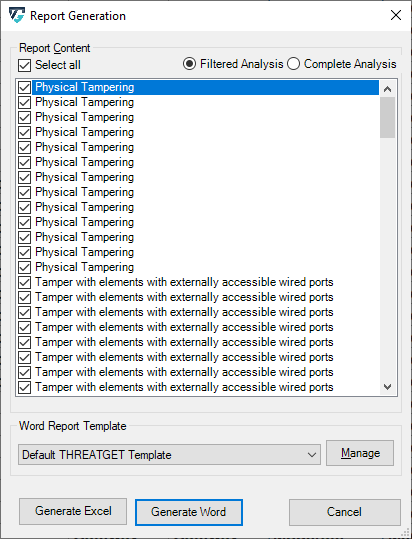
A full report of all results can be generated in Excel or Word format.
Excel Format
Click on the Generate Excel button to create full documentation of all results in an Excel format, as shown below.
***ThreatGet asks first the destination path for storing the generated report. ***
Word Format
Click on Generat Word to create full documentation of all results in a Word format, as shown below.
You also can select which report template to want to use. Otherwise, the "Default THREATGET Template" is selected by default.
ThreatGet asks first the destination path for storing the generated report.
Report Contents
The report contains a set of all obtained outcomes from the threat analysis process.
Main Page
When using the default template, the report's main page includes the ThreatGet's logo, version, the path of EA file (i.e., where the project is saved), author, and timestamp.

Table of Contents
The Table of Contents is described on the second page, showing the main parts of the generated report, as shown below.

The Main Model
The main model is displayed on the next page.
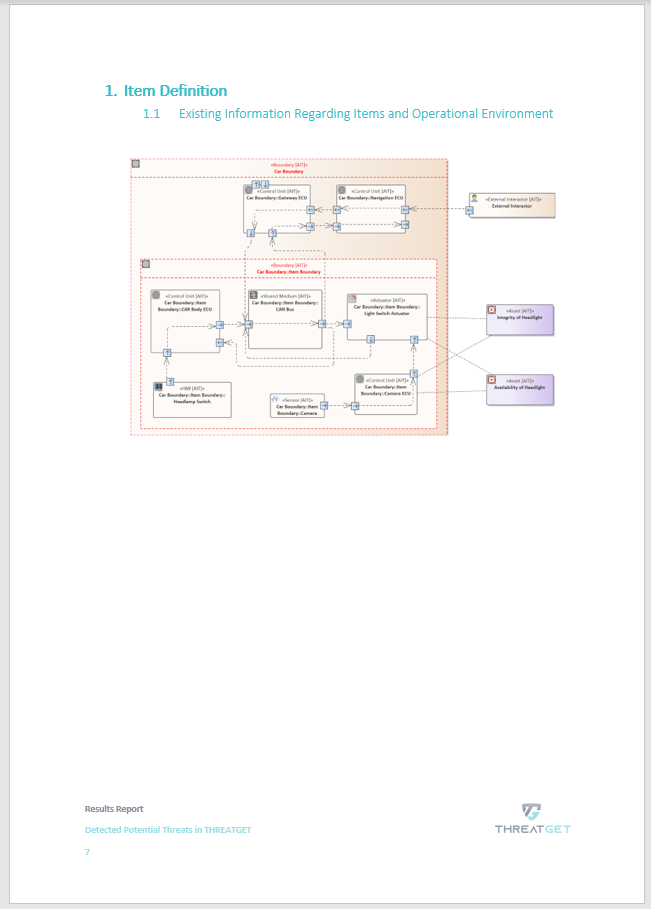
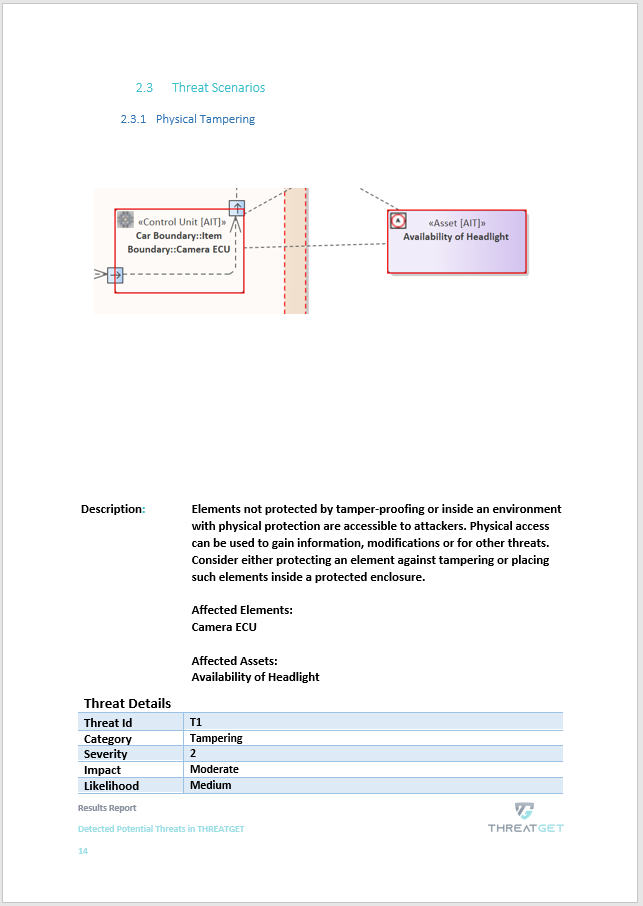
The Potential Threats
The other pages present more details about the identified threats, such as title, affected components(s), description, category, severity, impact, likelihood, and notes.
Risk Matrix and Summary
The Cyber Security risk assessment is summarized in the last two pages. It shows the risk, likelihood, impact & severity.
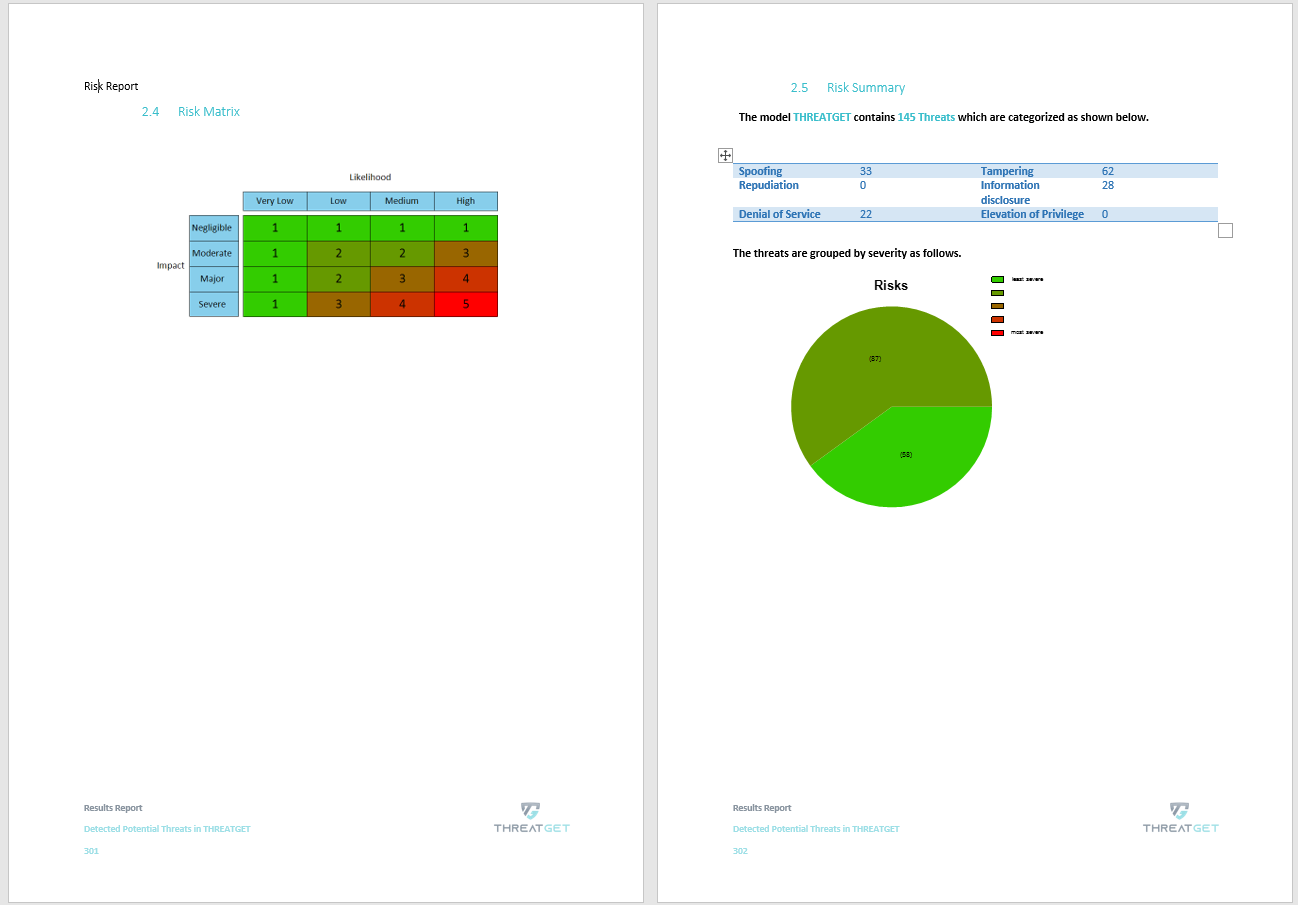
The summary of threats categories is defined on the last page of the report.
Template Management
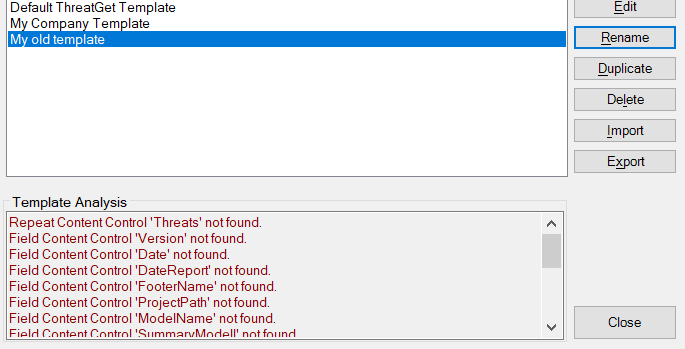
Using the Template Management dialog you can manage the report templates. Initially there is only one template: The "Default THREATGET Template"
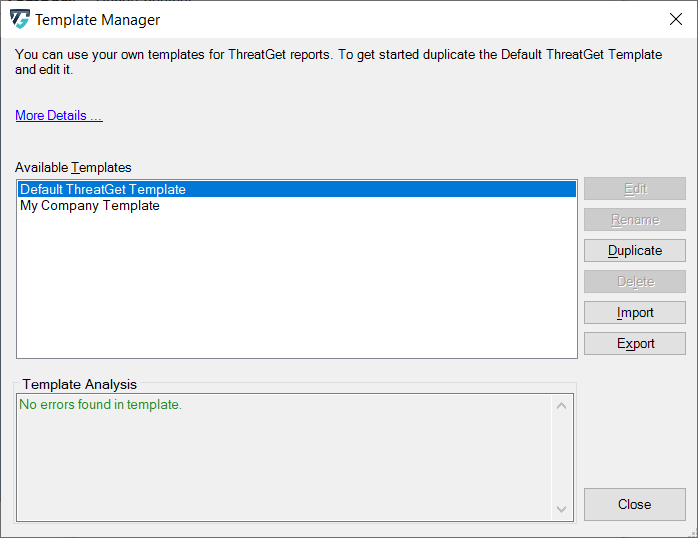
In the dialog there are two ways to add new templates. One is to import templates from the file system and the other is to duplicate an existing template. To create your first own template you would want to duplicate the "Default THREATGET Template".
Exporting and importing templates is useful to exchange templates between different users and computers.
In the lower half of the window problems the template may have are displayed. Problems could either be that the template is not a valid Word file or the Word file does not contain all the fields (see below). A template that does not contain all the fields can still be used to generate reports. The example below shows the analysis of an old template, where there are many fields missing.
Editing the template
You can edit a template by pressing the Edit button. You must have Microsoft Word installed to edit templates. If you do not have Microsoft Word the template may open in WordPad. WordPad is not suitable to edit templates and may destroy the template upon saving.
Templates work in principle by replacing fields of texts and images in the Word file with the threat images and descriptions. The first step is to activate design mode to make these replacement positions visible.
Activiting design mode
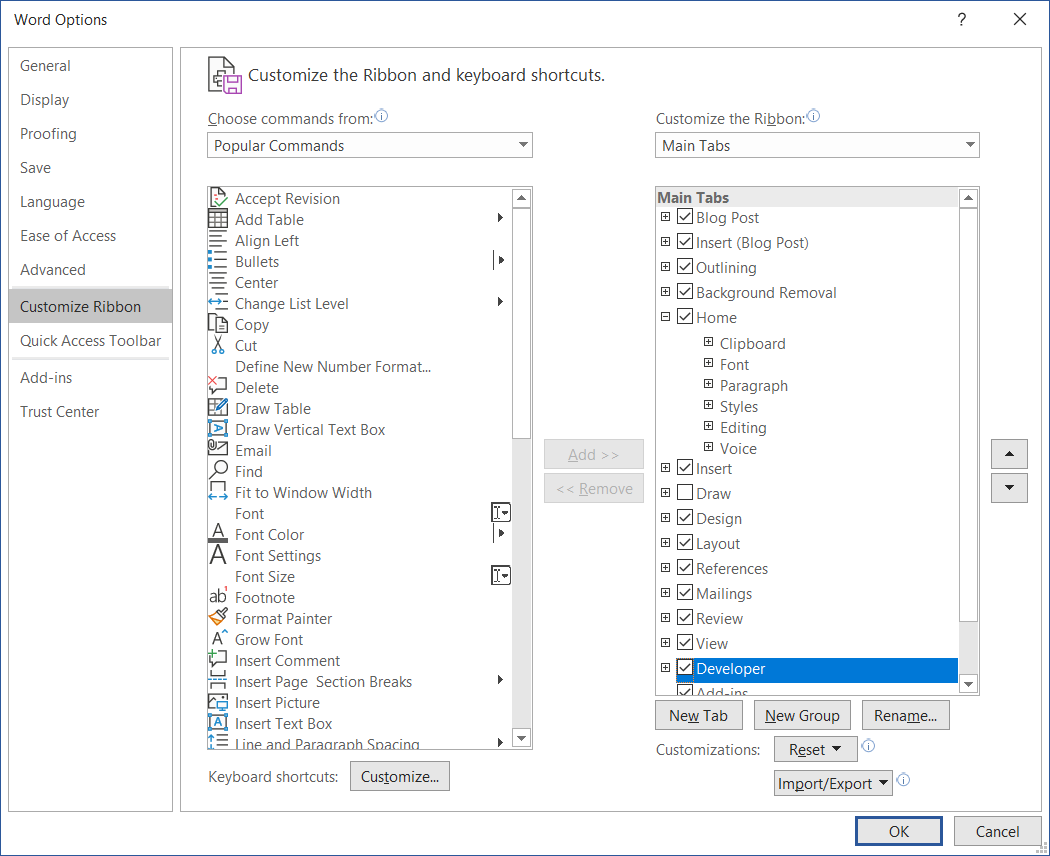
The first step is to display the Developer Tab in Word. This can be done by clicking on File and then on Options in the lower left corner. In the Options dialog you select Customize Ribbon and then select Developer as shown below.
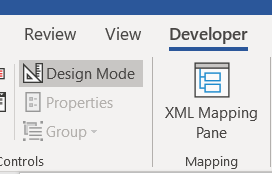
In the Developer tab you can activate Design Mode which will show the fields.
Replacement location
Replacements now are visible in the document itself.
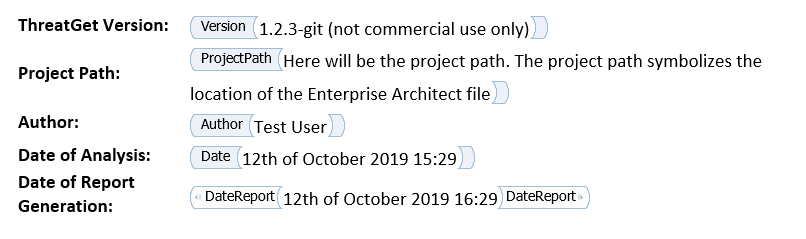
Every field is marked in Word. During report generation the text in the field will be replaced. The same goes for images inside fields, which are replaced as well. Images that are replaced are sized correctly such that they will not be displayed distorted in the generated report, even if they may seem distorted in the template.
The "Threat" field is special in that it is a repeating field. This means that everything between the "Threat" marks will be repreated for every threat detected. The "Threat" field spans the entire page.
Modifying the template
The fields can be moved around, copied or deleted. If a field is deleted this will show as a problem in the Template Management dialog. This does not inhibit usage of the template. If a field is duplicated both places will be replaced. It is not useful to add new fields as they will be ignored and their content will not be replaced during report generation.
The fields can be copied and pasted like normal text in Word.