Managing and Creating Diagrams
The updated version of ThreatGet provides flexibility to import an existing model (that was created using other ThreatGet versions, such as older versions) or create a new one entirely through the web interface.
Import Diagram
Importing existing diagrams is an extended feature in the new ThreatGet web interface, designed to facilitate the handling and manipulation of all diagrams, including those created by older ThreatGet versions. Therefore, if you have an existing diagram in the ThreatGet plug-in version, the new web interface version can import and handle these models. To do so, the user should already have the exported JSON file for the existing diagram and then select "Import Diagram...". More information about exporting existing models is described here.
Then select the file from the correct location where the file is already stored. Once the existing model is imported, it will be displayed on the web interface.
New Diagram
The user can model any diagram as needed using the web interface of the tool. The tool provides by default a set of components that can represent the system parts, each with a set of security properties representing a set of protections that can be activated as needed by the user according to the system's modeling requirements. All of these components and security properties can be extended by the user to add any more specific components or related properties that can model a complete designed model that mimics the reality of the system design. Another section in this documentation covers the way for managing and expanding components and security properties.
To see how the modeling process works, we expect to have the following model, which describes the Headlamp example, including multiple ECUs, a camera, an actuator, and connectors.
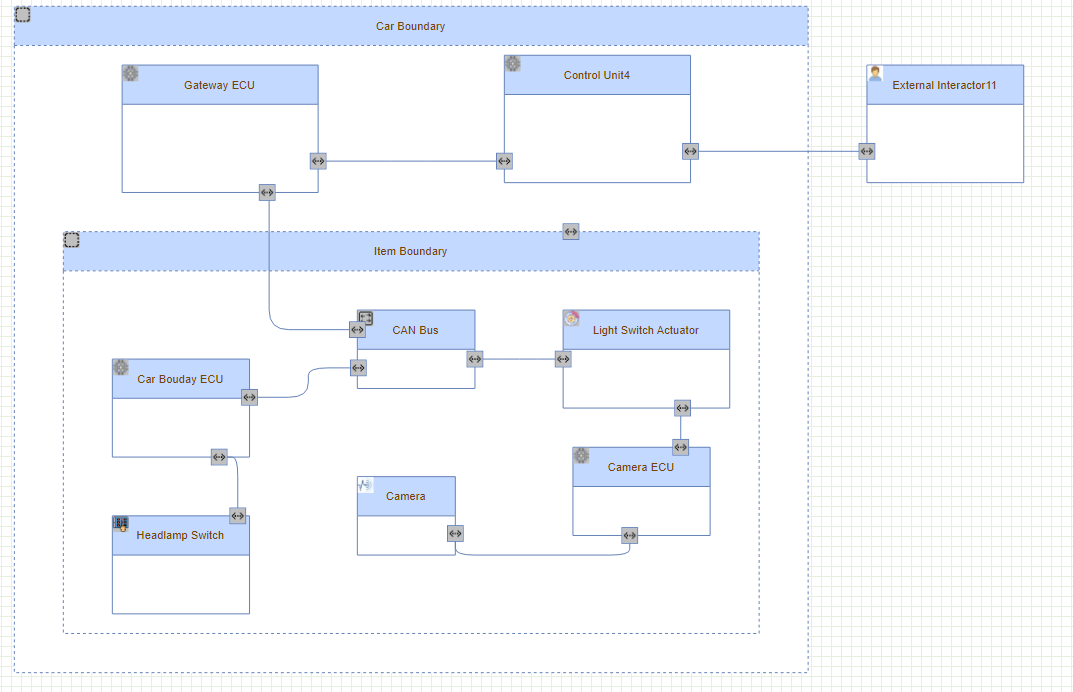
The following video shows steps for modelling the whole model.
To be continued in the same manner as shown in the video, by dragging and dropping components and defining the needed ports/connectors to describe the dataflow. The complete model will be finalized as illustrated in the following figure.
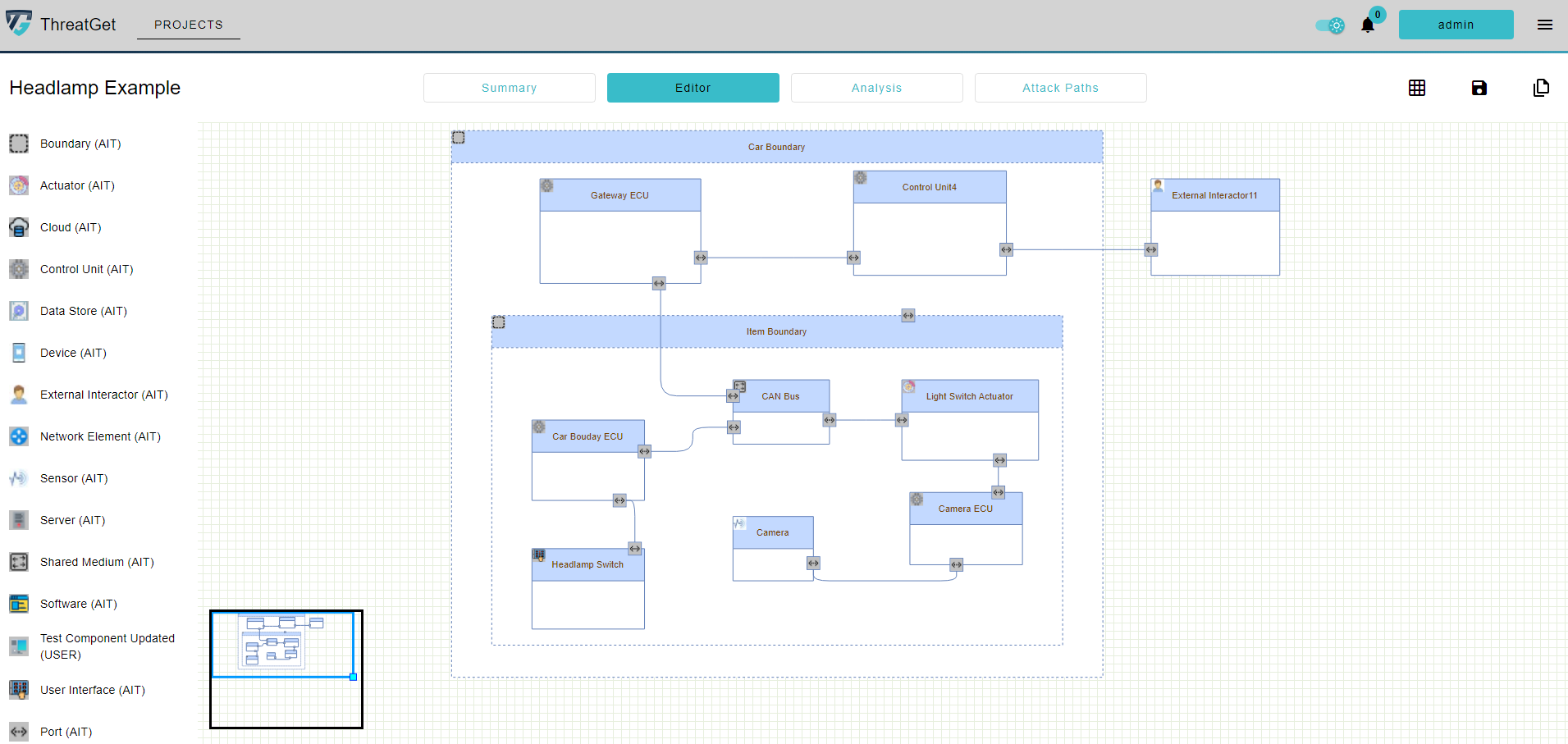
The figure Headlamp Example depicts two assets: "Integrity of Headlight" and "Availability of Headlight". Here we consider that we have these two assets and we need to assign them to the related system components (e.g., Light Switch Actuator and Camera ECU). So, if you press on the target element, a detailed list will be displayed on the right, where you can select the applicable existing assets from the asset list. Once you select the target asset, the letter A will be displayed on the upper right corner of the element, identifying that the element has asset(s).
The updated version of ThreatGet defines assets differently from the older version. Therefore, the user needs to describe assets at the project level as a whole, and perhaps define related damage scenarios. Then, describe the relation between them in a matrix form to determine damage scenario(s) for a particular asset. More details about creating assets and damage scenarios are covered in Assets and Damage Scenario.