Threat Analysis
Once the model has been completed, it is now the process of thoroughly investigating any potential cyber threats that could propagate through existing security vulnerabilities. The analysis can investigate potential threats in the system model using either normal analysis or attack path propagation. Thank you for the ThreatGet rule engine; it deeply examines potential weaknesses within the provided model.
Analysis Diagram
To begin the analysis, press the "Analysis" button as shown in the following diagram.
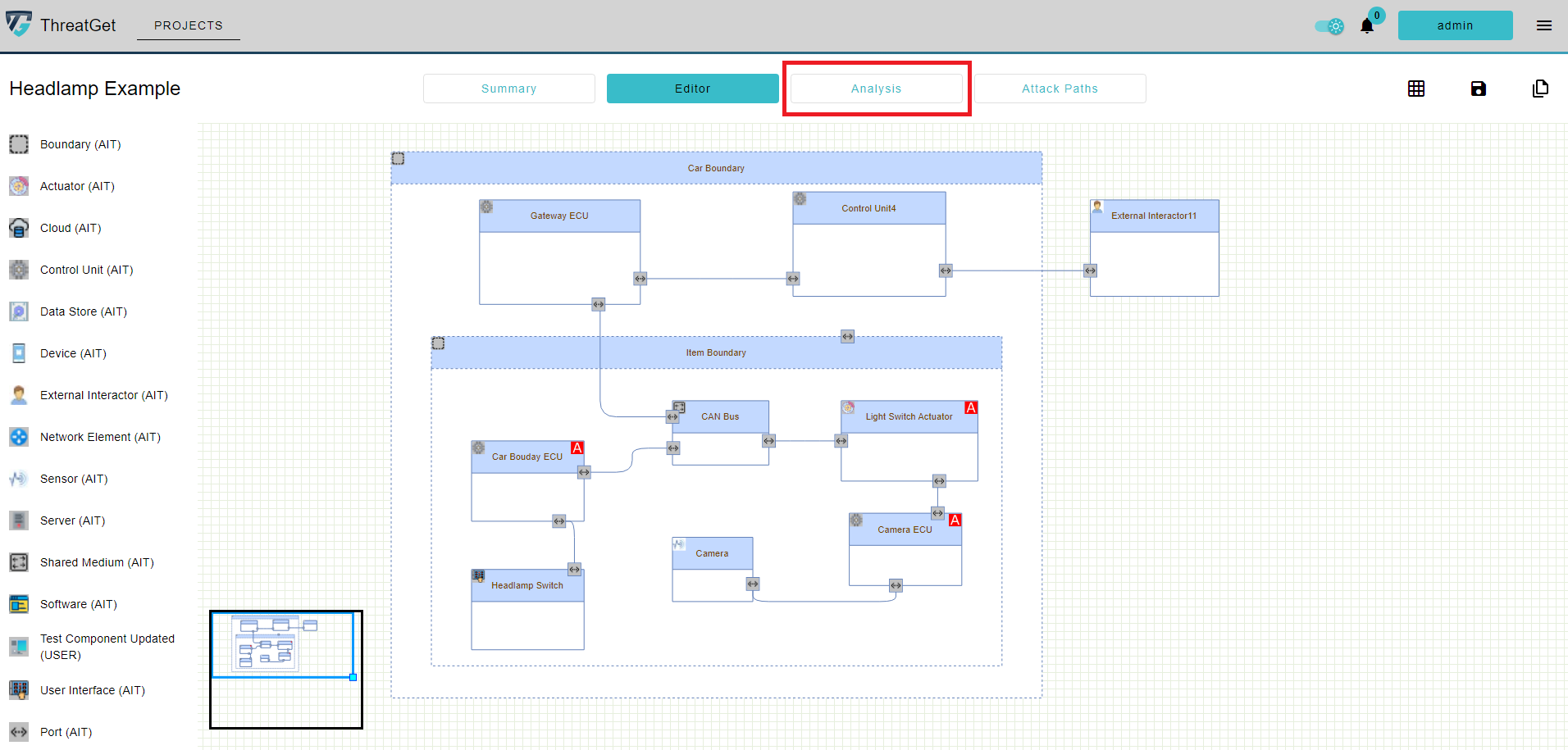
Another window is opened with different features that support the comprehensive analysis of any potential threats in the given model. Click on the "Magnifier" symbol to perform an analysis of the diagram.
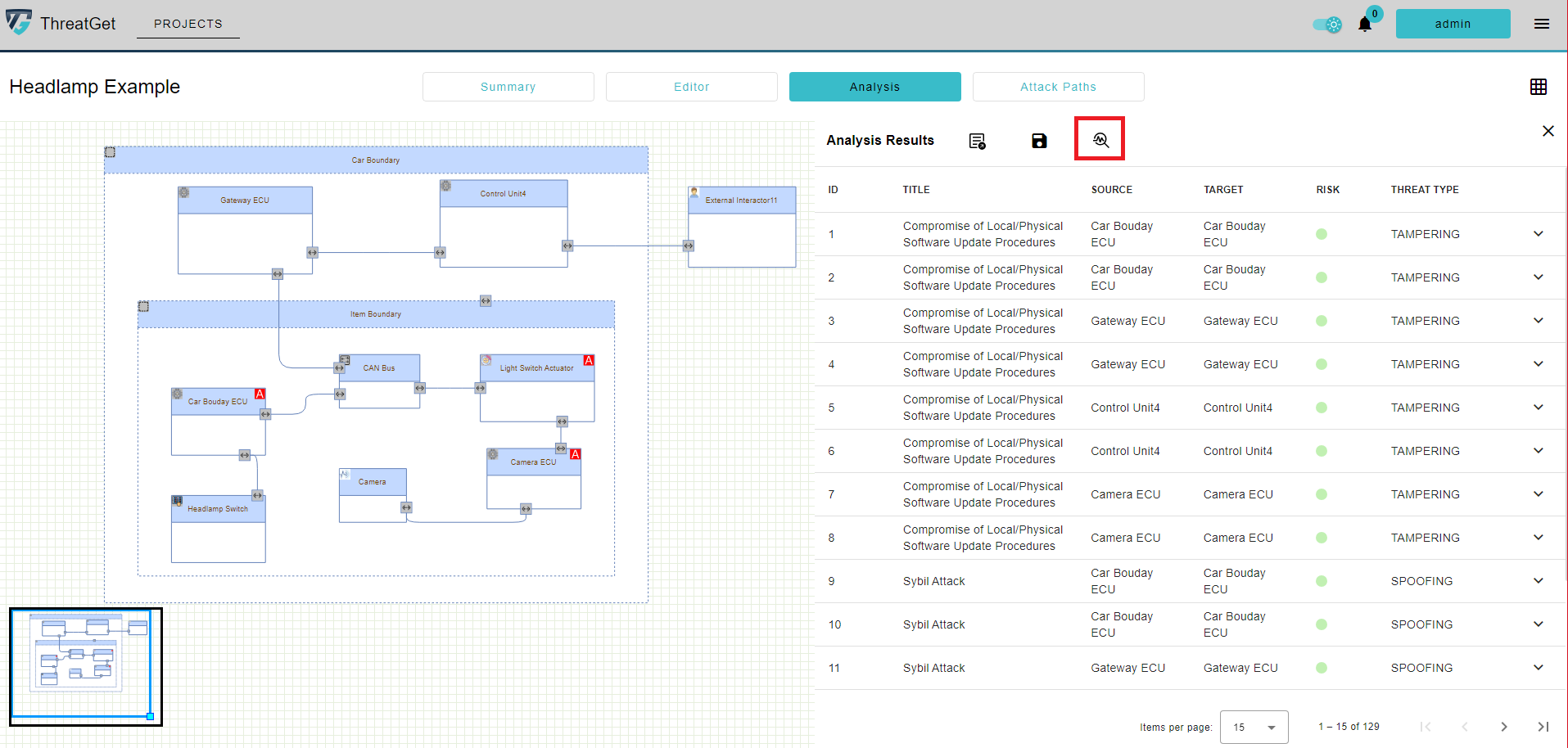
A group of identified threats will be listed on the right side of the current window, showing information about each threat as follows:
- Title: Name of the identified threat.
- Source: The affected source element.
- Target: The affected target element.
- Risk: Risk level based on automatically determined cyber risk.
- Threat Type: Each threat is classified according to its malicious impact; ThreatGet uses the STRIDE model to describe the category of all identified threats:
- S – Spoofing: violates authentication
- T – Tampering: violates integrity
- R – Repudiation: violates non-repudiation
- I – Information Disclosure: violates confidentiality
- D – Denial of Service: violates availability
- E – Elevation of Privilege: violates authorization
For more details on each threat, press of the threat, the window will be extended with more details.
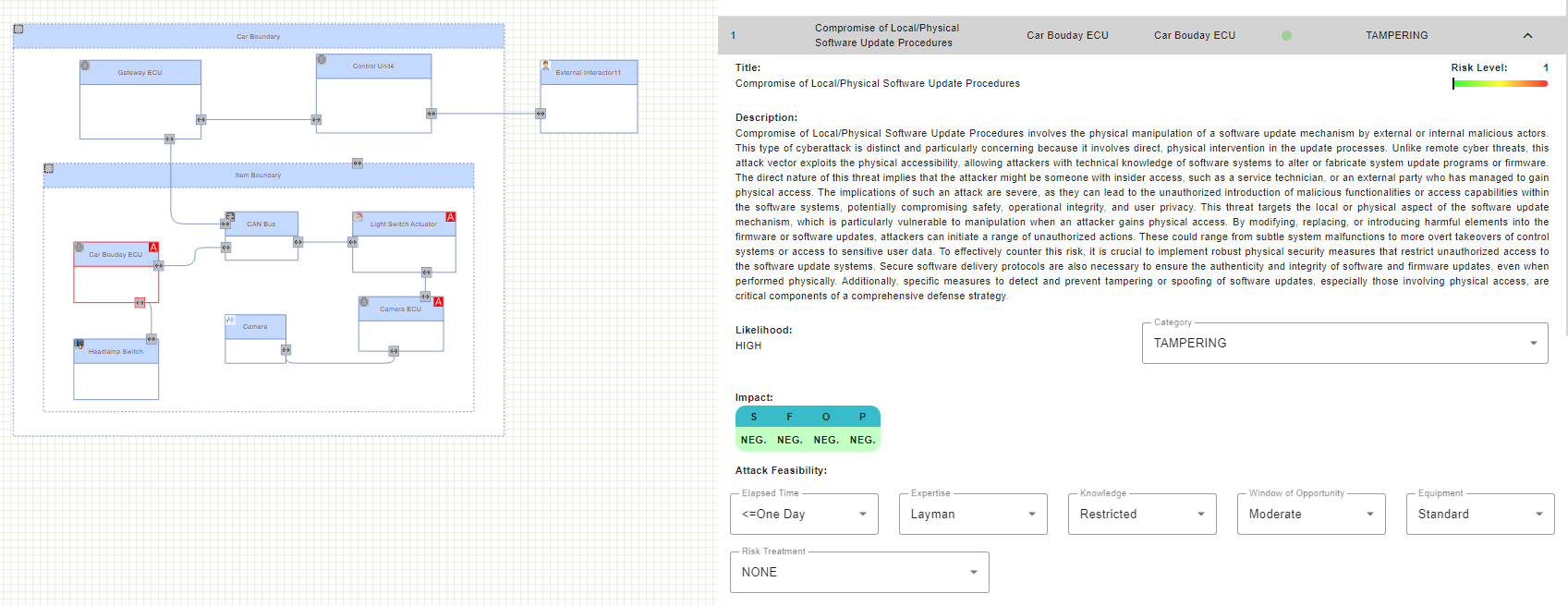
The Description field offers further information about the threat and elaborates on the particular elements and connections that have been impacted by the selected threat.The Risk Level shows the degree of risk based on the defined values of the Likelihood and Impact of each threat. Also, the Category shows the STRIDE category of the threat. The user can change the Category by selecting the desired through the menue.
The Attack Feasibility describes multiple attributes indicating the feasibility of a successful attack. According to ISO 21434, this includes the following:
-
Elapsed Time: Represents the time to identify and exploit vulnerabilities for an attack, which can range from days to months.
-
Expertise: Capabilities of attackers, which can vary as follows:
- Layman: Unknowledgeable with no expertise.
- Proficient: Knowledgeable with familiarity with security behavior.
- Expert: Familiar with algorithms, protocols, hardware, structures, and security techniques.
- Multiple Experts: Multiple highly experienced engineers with expertise in different fields.
-
Knowledge: It represents the knowledge about the target, varying based on available information.
- Public: Public or shared information, such as data shared on the internet.
- Restricted: Internal documents shared between restricted parties.
- Confidential: Confidential information about the item itself.
- Strictly confidential: Strictly confidential information about the item itself.
-
Window of opportunity: This represents access type (physical or virtual) and time spent accessing the target (limited or unlimited), including various levels:
- Unlimited: Highly available through untrusted or public networks without a time limit.
- Easy: Highly available with limited-time access.
- Moderate: Have restricted limits for access using special tools or methods.
- Difficult: Very low availability, with limited windows of opportunity for performing an attack.
-
Equipment: Describes attack tool classifications:
- Standard: This type of equipment is available to attackers, and it could also be part of the target item itself, such as debuggers in Operating Systems.
- Specialized: It is equipment that is not easily available to attackers but can be acquired with effort.
- Bespoke: This type of equipment is not available to the public, such as specific manufacturer-restricted tools.
- Multi Bespoke: Refers to bespoke equipment for various attack stages.
-
Risk Treatment: Defines the proper action that should be taken for handling the cyber risk. The user can define their decision for controlling the risk, which can be classified into four different actions:
- Accept: No particular action is required.
- Mitigate: Specific actions should be taken to keep the risk low or at an acceptable level.
- Transfer: This action involves transferring the risk to someone or an organization capable of managing and controlling it.
- Avoid: Refers to avoiding cyber risks by applying security measures to prevent any negative consequences.
Note: Please note that any changes or updates in the model should be saved; otherwise, the user will lose all changes. Therefore, once the user has made changes, the save button should be pressed. After identifying all threats, the user can generate a report containing these results. Generating reports is covered in Section Report Generation. In addition, the tool offers a Summary of the outcomes of the threat analysis process.
Attack Path
This kind of analysis aims to identify a potential attack path, if multiple attack paths are possible. It shows the possible paths that an attacker can follow to reach a malicious goal. Referring to our example (e.g., Headlamp example), the following illustrates a simple example of the propagation of threats through an attack.
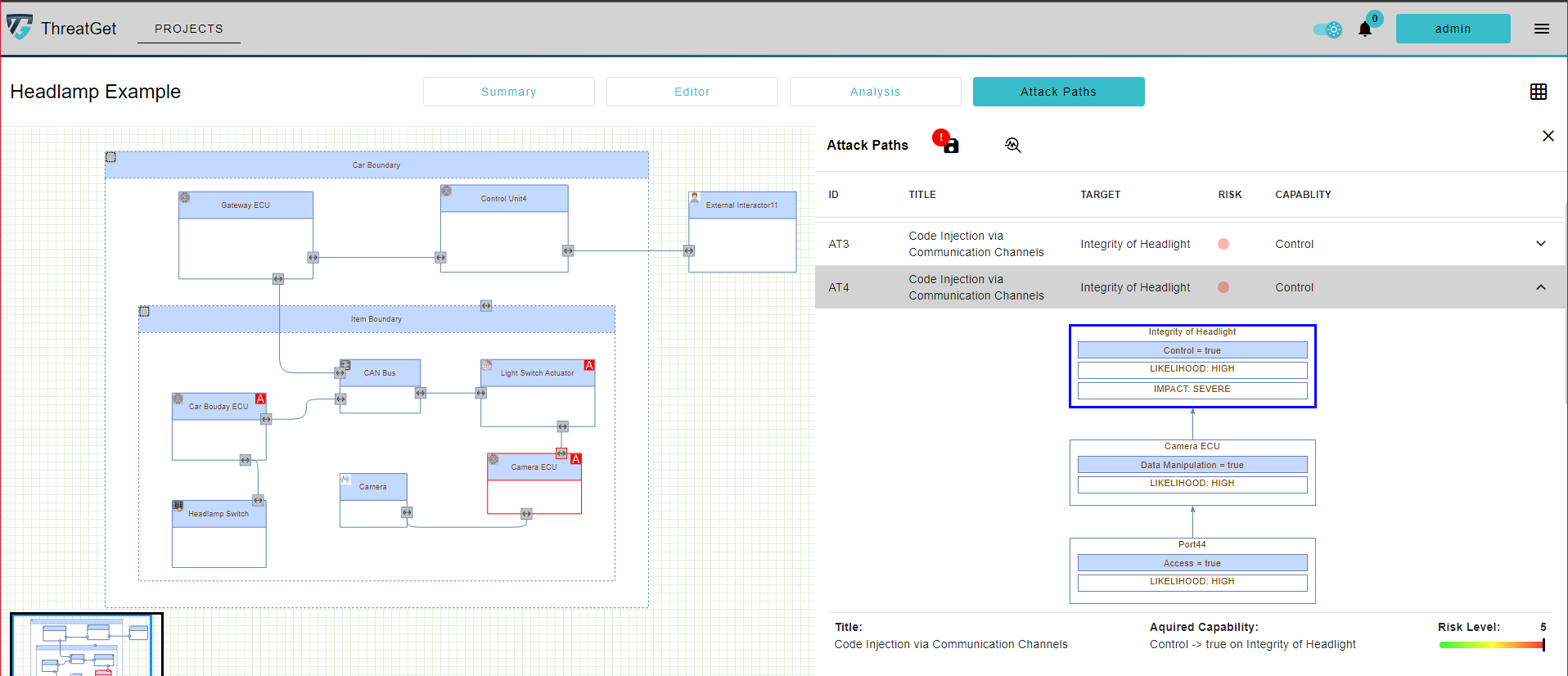
This attack shows the beginning of a cyberattack, highlighting the existing weak or disabled security properties that triggered this kind of attack. The attack propagates until reaching the target impacted component. The main vulnerable component in this type of attack path analysis is the asset.