Managing Rules
There are essentially two parts for an Analysis with THREATGET. The first part contains the creation of a System Model inside the Enterprise Architect Plugin. The second part deals with the creation and maintenance of the Rule Database. The following section shows how you can manage and create rules. You can only change or delete the rules you have created yourself. The rules provided by the AIT cannot be edited.
Create a New Rule
To create a new Rule, you first have to switch to the correct overview. Do so by clicking on Rules in the navigation bar.
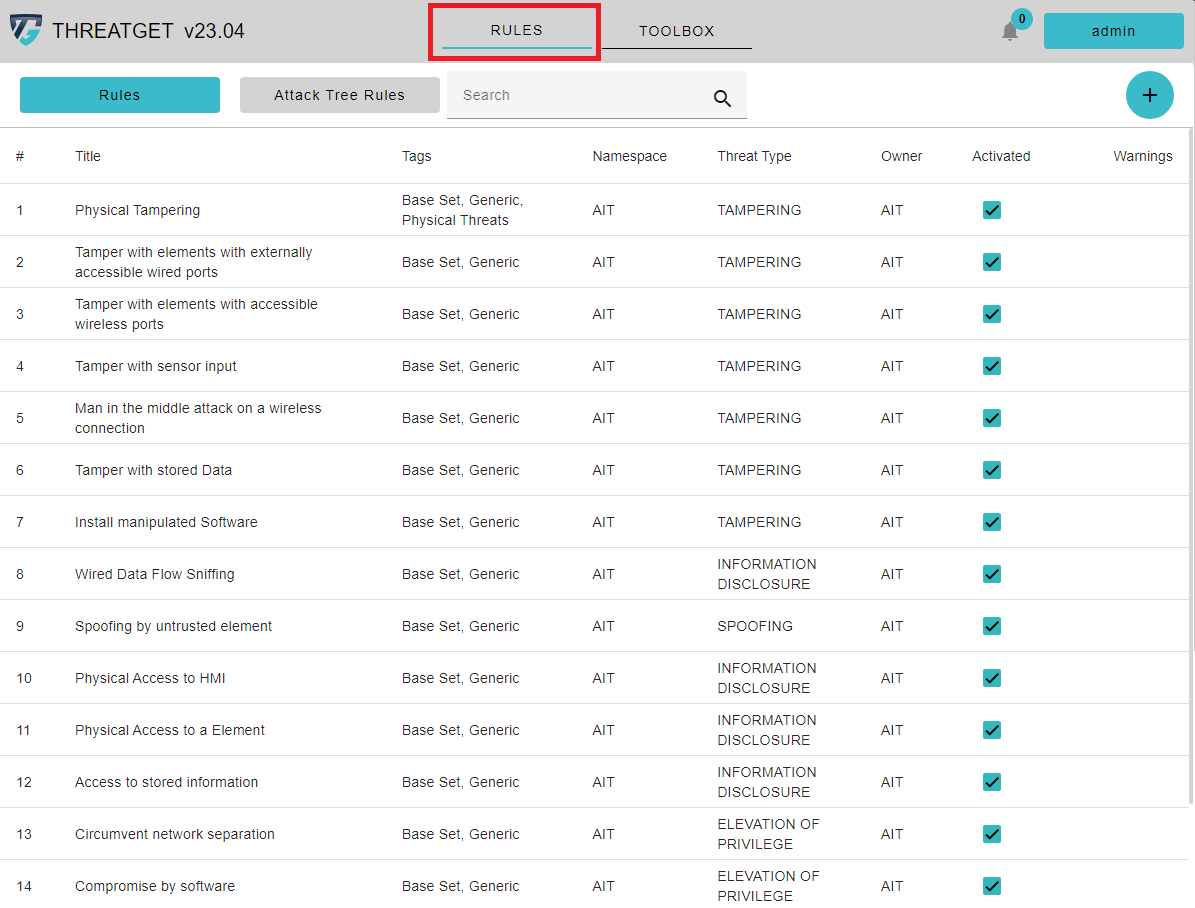
All previously created rules are listed in this list. Each rule has the following attributes: Title, Tags, Namespace, Threat Type, Owner, Activated, and Warning. The checkboxes for activation are used to activate rules that are required throughout the threat analysis process. As a result, you can quickly uncheck the checkbox in the Activated column to ignore the rule(s) in the analysis.
In the upper left corner you will see two buttons. These allow you to switch between Normal Rules and the Attack Tree Rules. When creating a rule, it is automatically decided whether a rule can be used during an attack analysis or is only meant for single, independent analysis approaches.
If you hover over one of your own rules, a Trash Can button appears to delete it. To view or edit rules, simply click on the row of the desired one. AIT Rules can only be viewed.
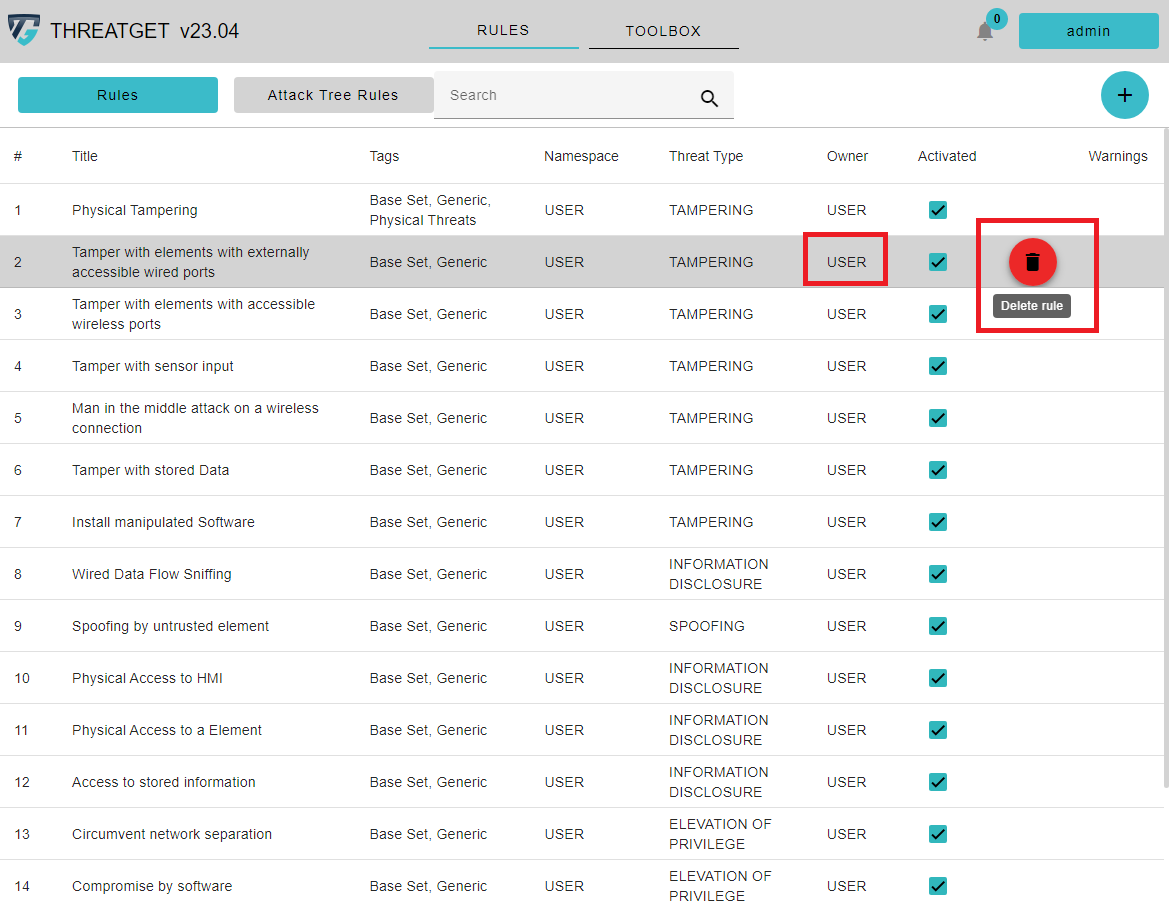
To create a new rule please click on the + button on the right upper corner.
Rule Details
This opens the Rule Editor window, which includes two primary tabs. Title, Description, Tags, Threat Type, Likelihood, and Impact are all provided in the first tap Definition.
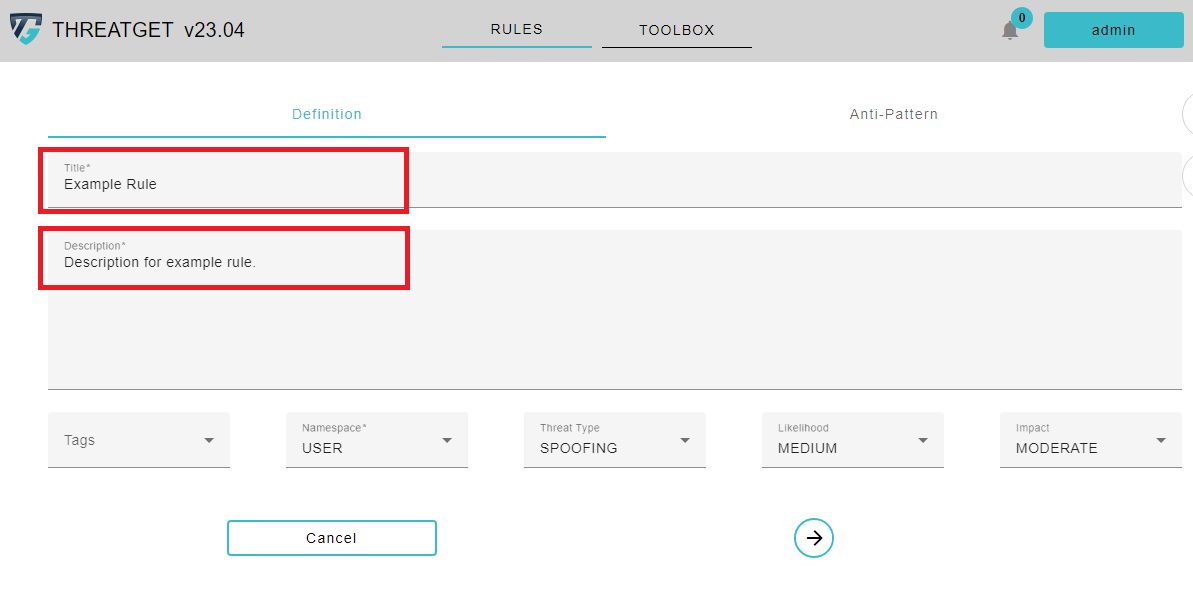
The ThreatType follows the STRIDE standard. STRIDE is a model of threats developed for identifying computer security threats.
STRIDE:
* Spoofing
* Tampering
* Repudiation
* Information disclosure
* Denial of Service
* Elevation of Privilege
* UNECE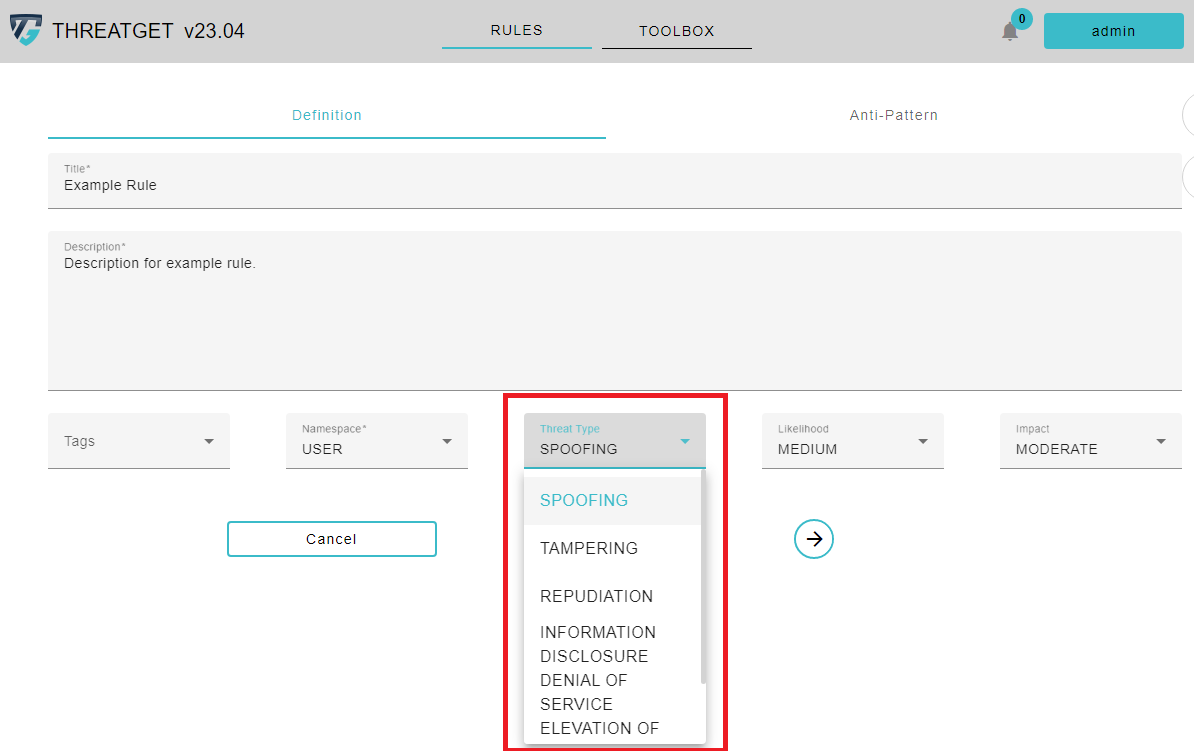
Please click on the Threat Type button and select, in this case, Elevation of Privilege in the appearing Dropdown menu cause we want to check if we provide some ** Authorization** as we described inside the description. ThreatGet estimates the risk severity of this threat; by utilizing the parameter values of the impact and likelihood.
The Likelihood in TheatGet has four levels:
* VERY LOW
* LOW
* MEDIUM
* HIGH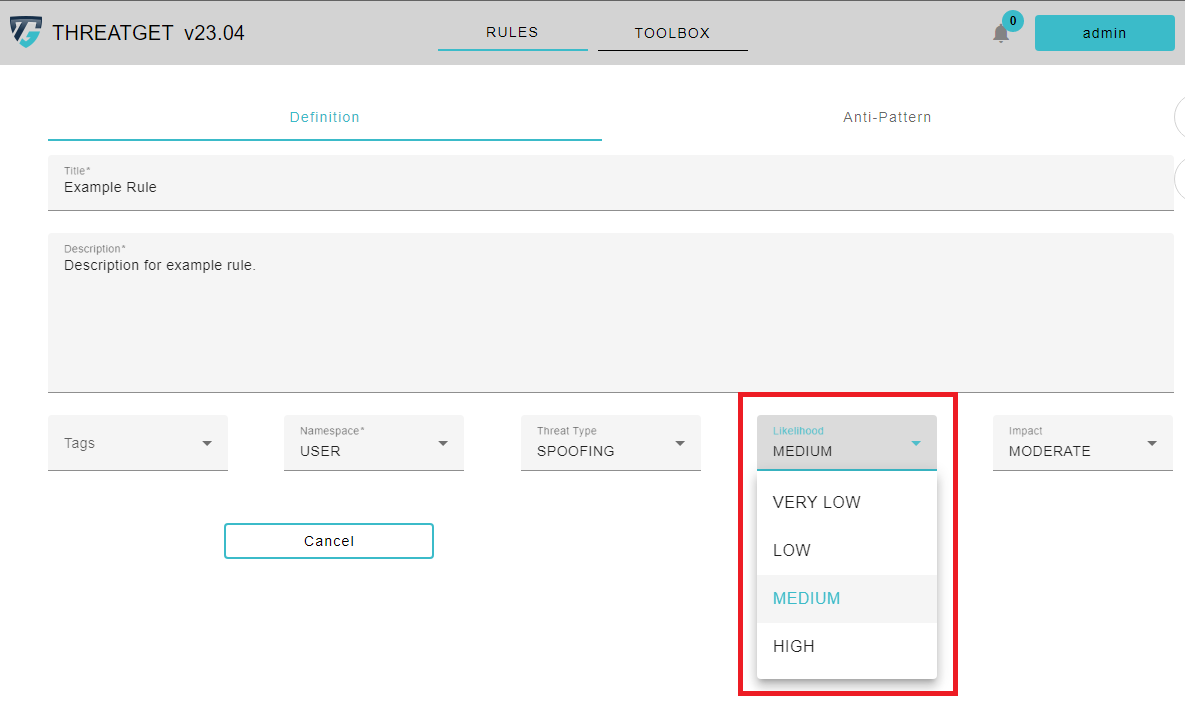
The Impact in ThreatGet has four levels:
* NEGLIGIBLE
* MODERATE
* MAJOR
* SEVERE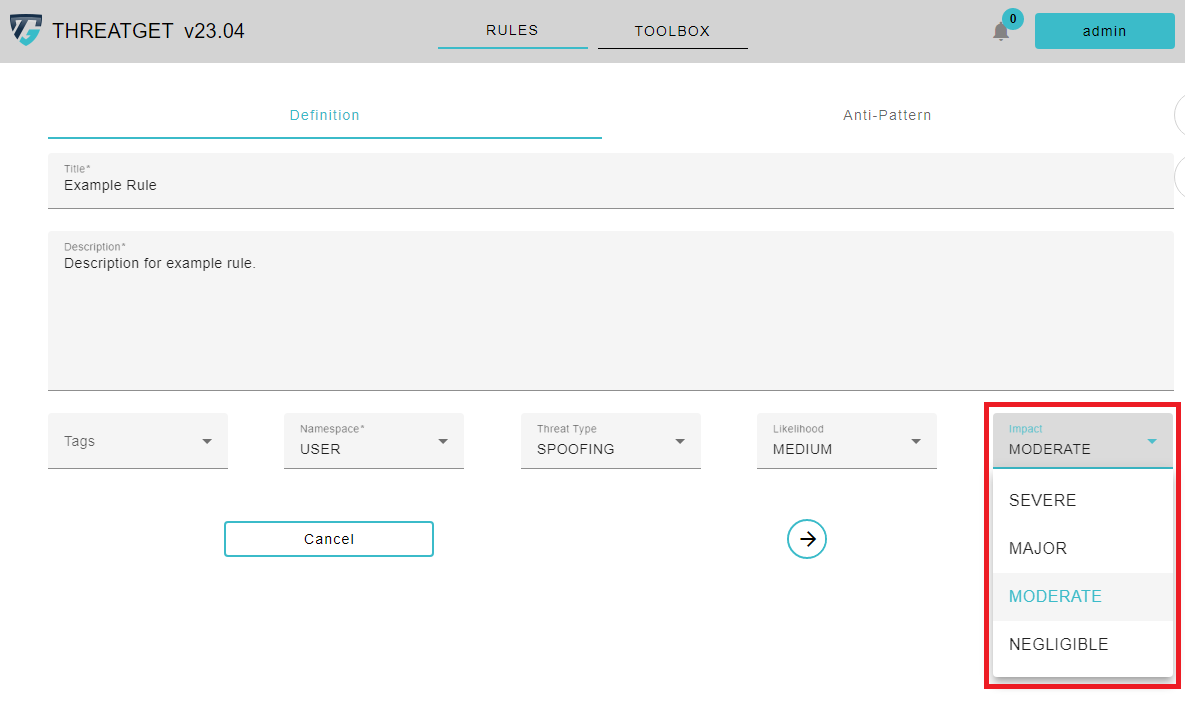
In our example, we suggest selecting a MEDIUM value for the likelihood and MODERATE value for impact. You can also add Tags to your Rule. These tags are different from the Tagged Values. The purpose of the THREATGET Tags is to group Rules into categories. To add a Tag to a Rule please click on the selectable Tags. To learn how to create new THREATGET Tags please see the documentation for tag creation.
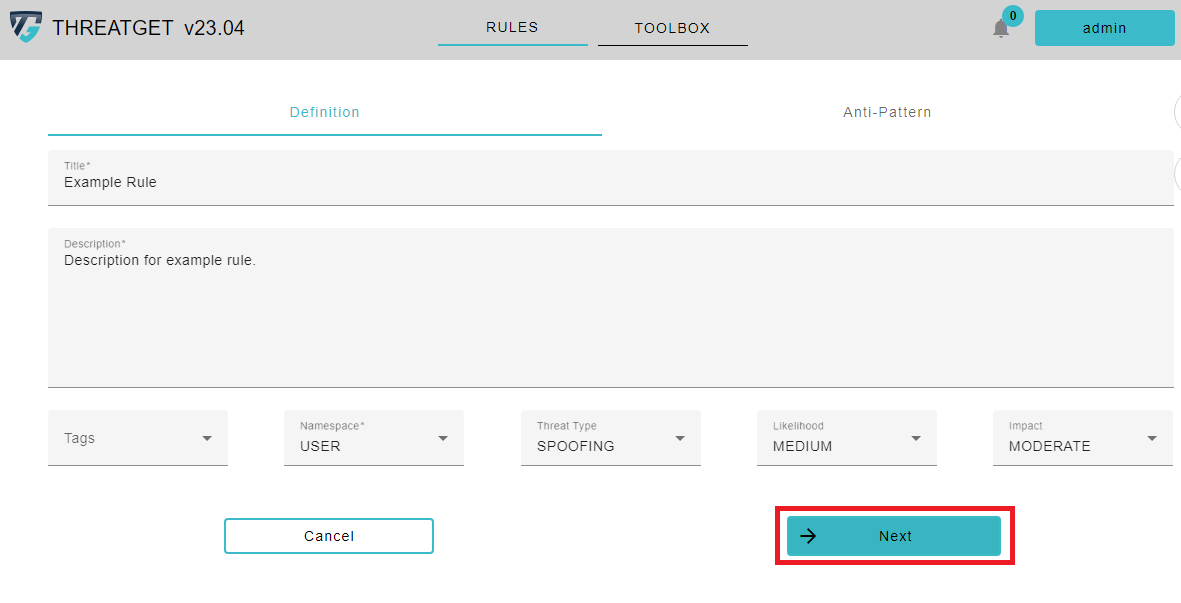
Then press Next to proceed into the following step, which is writing the rule text.
Rule Text
The second tap Anti-Pattern is used to write the main rule text. In our example, we will check the Authorization tagged value of the Top Element.
ELEMENT : "Top Element" {
HAS ATTRIBUTE "Authentication" != "Strong"
}
To learn how the Syntax of rules works please see the documentation for rule creation. If you have filled out everything you can click on the Check button at the buttom of the screen.
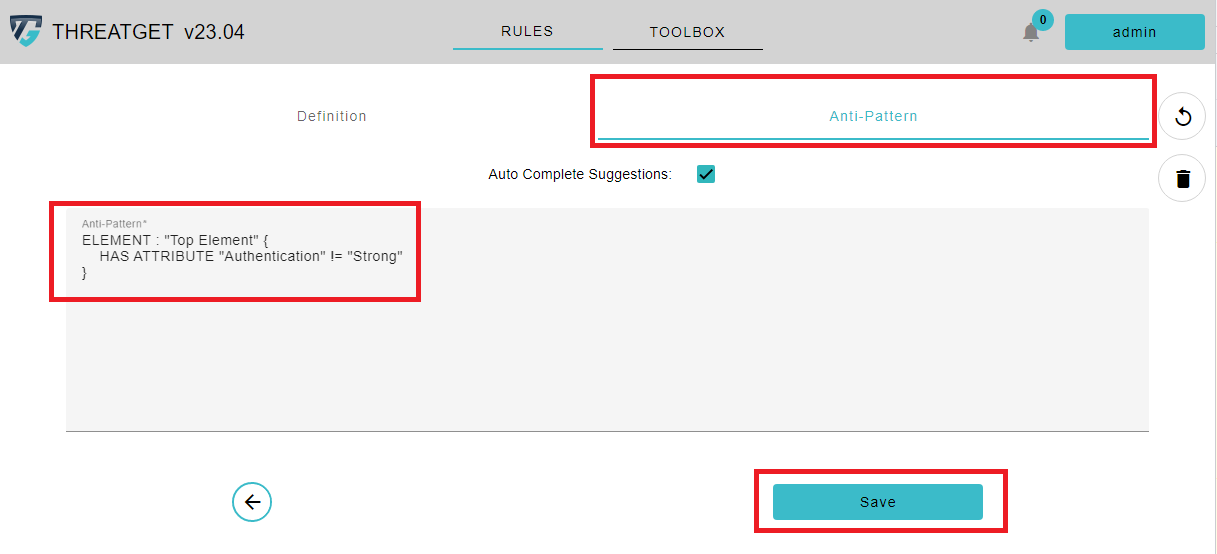
The application now checks in the background whether your entered rule is syntactically correct. As you can see, the Check button got replaced with a Save button. This means that the rule was syntactically correct and can now be saved. The saved rule is saved in the rule database and is listed with the other previously saved rules.
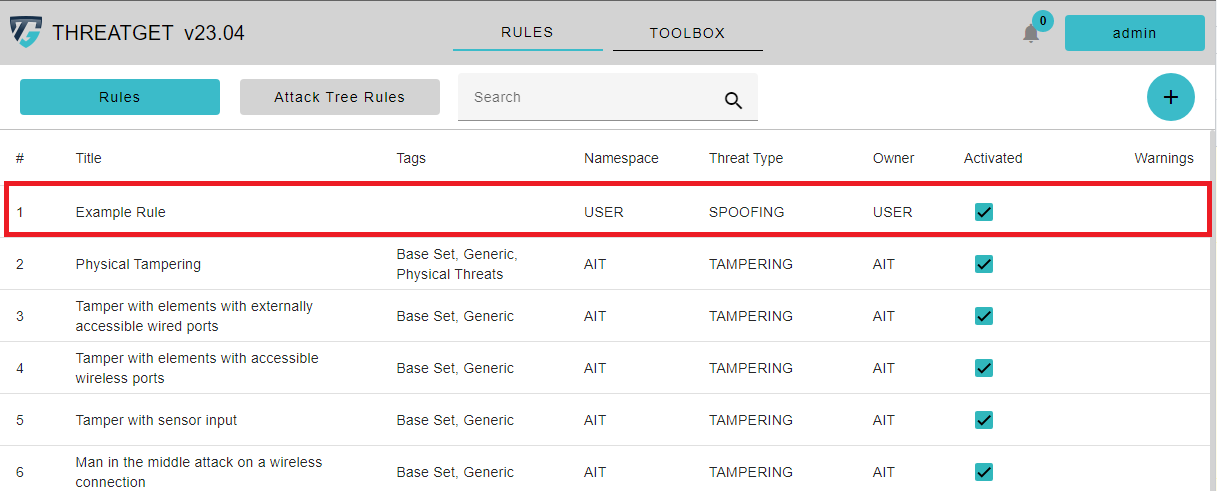
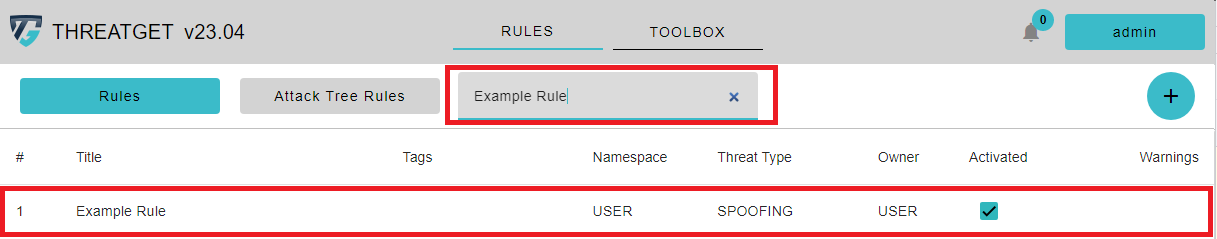
If you hover over the rule, you can see a Trash Can button. By clicking on the row of the rule in the table, you can EDIT this rule. By clicking the Trash Can button, you can DELETE this rule. You can see the added THREATGET Tags next to the name of the Rule. You are also able to search for rules with certain tags inside the Search Bar above.
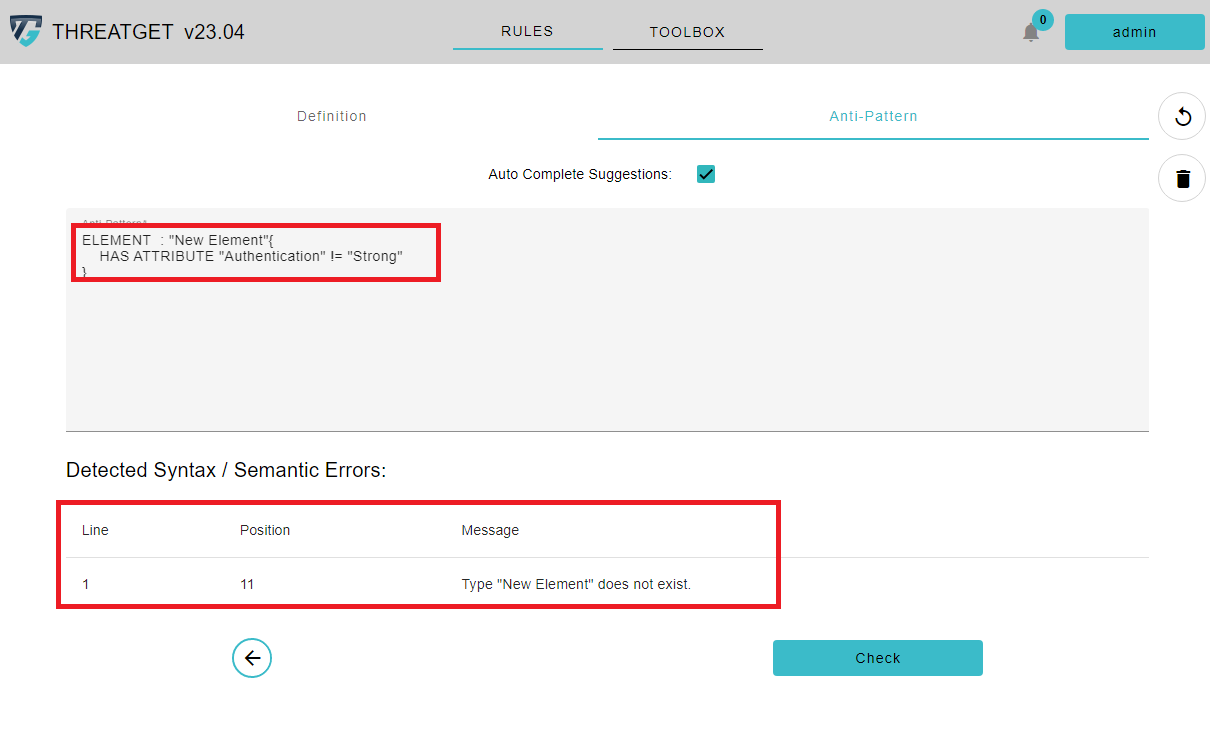
However, if the rule text has an error, say the user defines a name of a non-existing element, a table with the error type and more information appears on the screen.
ELEMENT : "New Element" {
HAS ATTRIBUTE "Authentication" != "Strong"
}
As you can see, the Type "New Element" does not exist is now displayed. There you can see the line where the error occured and what was wrong
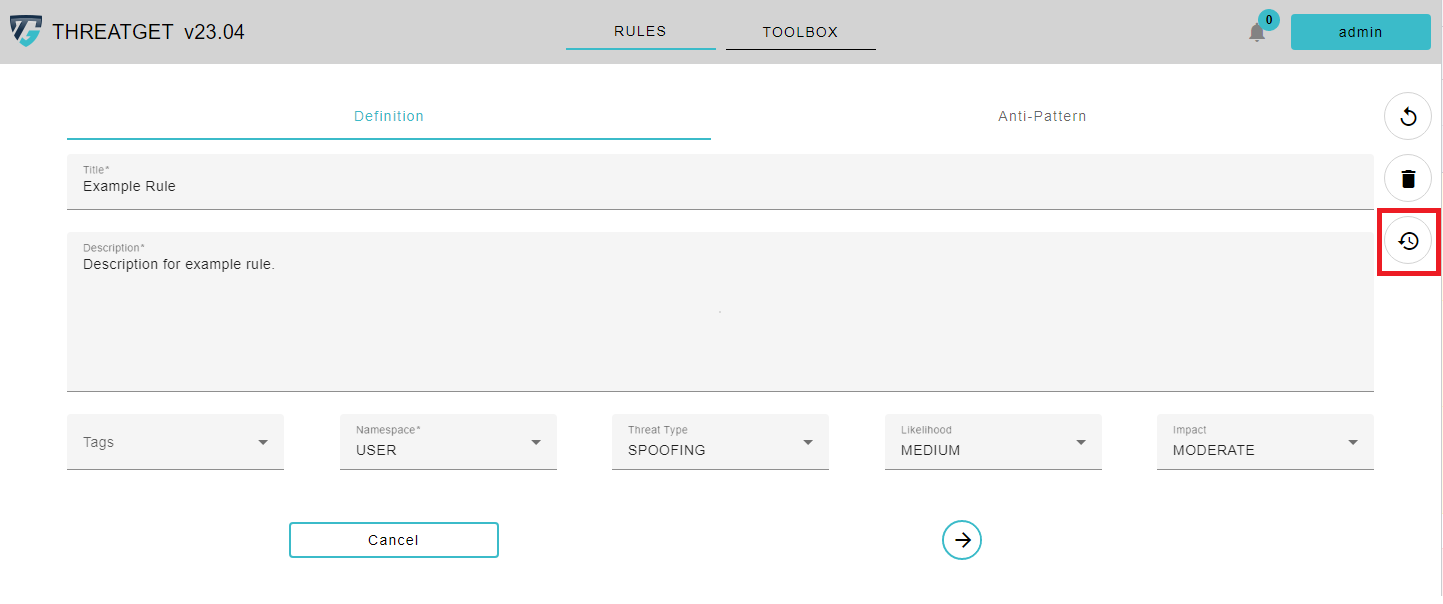
View History of a Rule
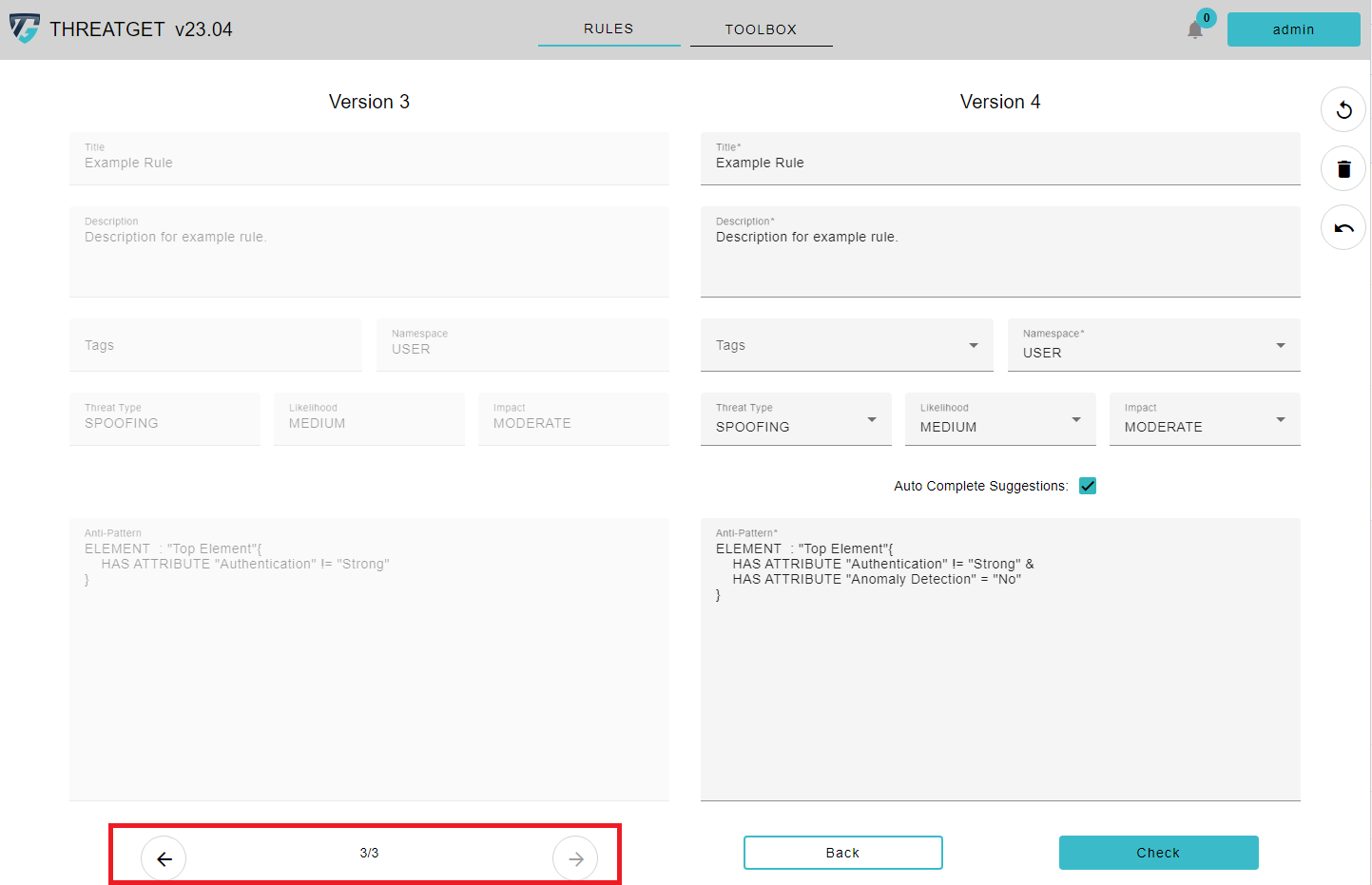
Threatget also has a history function for the rules. Over time, you may change a rule several times and adapt it for new circumstances. As soon as you update a rule, you can view the past versions in the rule editor. To do this, first click on a rule you have created to edit it and then click on the Reverse Clock symbol.
On the left side you can see the past versions, which you cannot change. On the left side you can see the rule, which you can edit. If you want to see another version, you can use the Arrow buttons to switch between the versions.